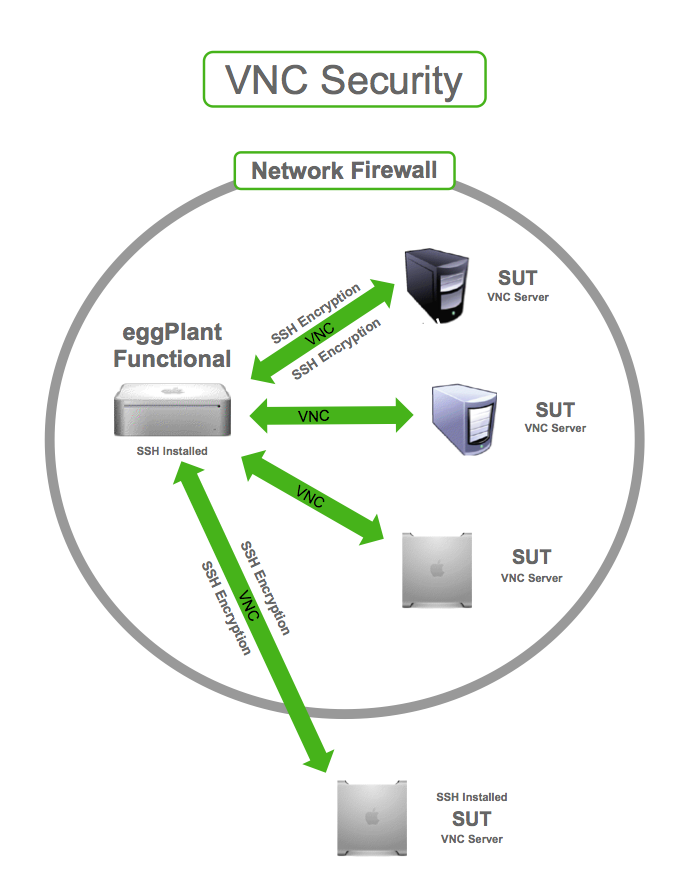
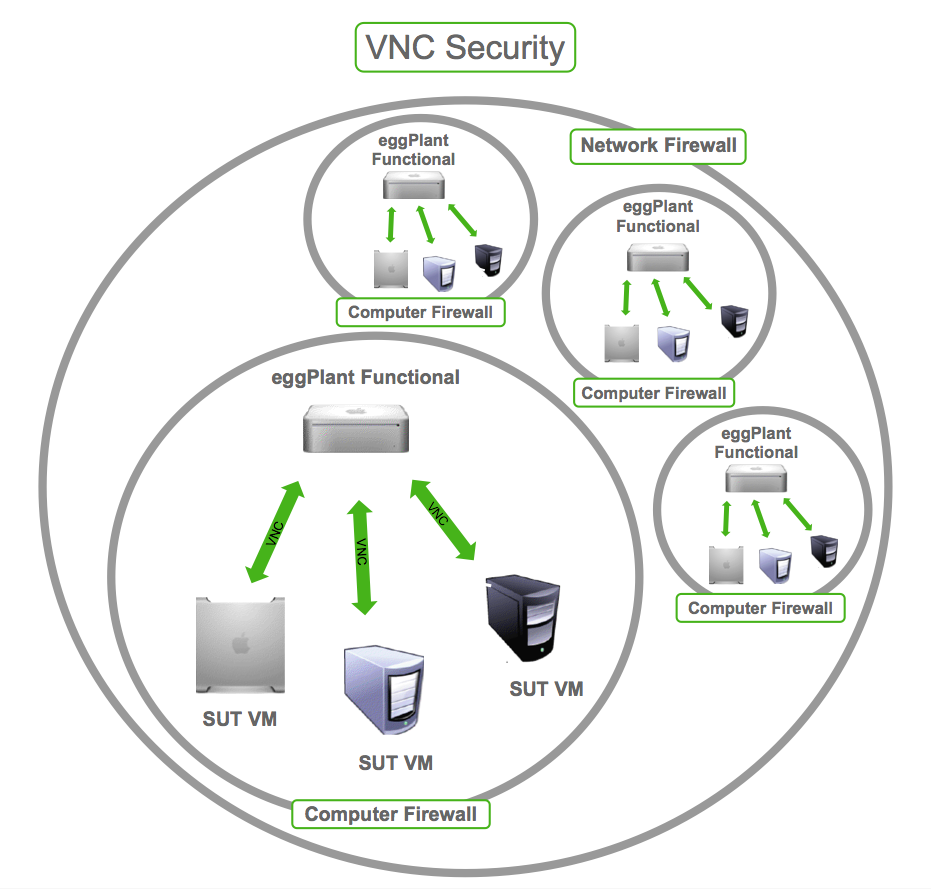
In today's digital landscape, remote access tools like VNC (Virtual Network Computing) have become essential for businesses and individuals alike. VNC security risk issues, however, pose significant challenges that must be addressed to ensure safe and secure remote connectivity. Understanding these risks is critical to protecting sensitive data and maintaining system integrity.
As more organizations adopt remote work strategies, the reliance on VNC technology has grown exponentially. While VNC offers unparalleled convenience and flexibility, its vulnerabilities can expose users to cyber threats if proper security measures are not implemented. This article delves into the various security risks associated with VNC and provides actionable solutions to mitigate them.
By exploring real-world examples, expert insights, and best practices, this comprehensive guide aims to equip readers with the knowledge needed to enhance their VNC security posture. Whether you're a system administrator, IT professional, or an individual user, understanding VNC security risk issues is vital for safeguarding your digital environment.
Read also:Hoka Cosmic Pearl Bondi 8 The Ultimate Guide To Comfort And Performance
Table of Contents
- Introduction to VNC
- VNC Security Overview
- Common VNC Security Risks
- Password Management
- Encryption Standards
- VNC Attack Vectors
- Best Practices for VNC Security
- Tools for Securing VNC
- Real-World Case Studies
- Future of VNC Security
- Conclusion and Next Steps
Introduction to VNC
VNC is a widely used remote desktop protocol that allows users to control and interact with a computer remotely. Developed in the late 1990s, VNC has evolved into a versatile tool for remote administration, technical support, and collaborative work. However, as with any technology, VNC security risk issues can arise if proper precautions are not taken.
The core functionality of VNC relies on a client-server architecture, where a VNC server runs on the remote machine and a VNC client is used to access it. While this setup provides convenience, it also introduces potential vulnerabilities that malicious actors can exploit. Understanding the underlying mechanics of VNC is crucial for identifying and addressing these risks.
For instance, VNC's default configurations often lack robust security features, making it susceptible to unauthorized access. This section explores the fundamental aspects of VNC and highlights why security should be a top priority for users.
VNC Security Overview
Importance of Securing VNC Connections
Securing VNC connections is paramount due to the sensitive nature of the data being accessed. Whether it's confidential business information or personal user data, the potential consequences of a VNC security breach can be devastating. Organizations must implement comprehensive security strategies to protect their networks and systems from unauthorized access.
According to a report by the National Institute of Standards and Technology (NIST), remote access tools are one of the most targeted vectors for cyberattacks. This highlights the need for robust security measures when using VNC. By prioritizing VNC security, users can significantly reduce the risk of data breaches and other malicious activities.
Common VNC Security Risks
Unsecured Connections
One of the primary VNC security risk issues stems from unsecured connections. By default, many VNC implementations do not use encryption, leaving data transmissions vulnerable to interception. Attackers can exploit this weakness to eavesdrop on communications or even gain unauthorized access to systems.
Read also:Curling Wand Accessory Transform Your Hairstyle With These Essential Tools
Weak Passwords
Poor password management is another common vulnerability in VNC setups. Using weak or default passwords makes it easier for hackers to compromise VNC sessions. It is essential to enforce strong password policies and regularly update credentials to enhance security.
Malware and Exploits
VNC clients and servers can also be targeted by malware and exploits designed to compromise system integrity. Keeping software up to date with the latest security patches is crucial for mitigating these risks. Regularly monitoring for suspicious activity can help detect and respond to potential threats promptly.
Password Management
Effective password management is a cornerstone of VNC security. Implementing strong password policies and utilizing multi-factor authentication (MFA) can significantly enhance the security of VNC connections. Below are some best practices for managing VNC passwords:
- Use complex passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
- Avoid using easily guessable information such as names, dates, or common words.
- Change passwords regularly and avoid reusing old ones.
- Enable MFA to add an extra layer of security to VNC logins.
By adhering to these guidelines, users can minimize the risk of unauthorized access and protect their VNC sessions from potential threats.
Encryption Standards
Encryption plays a vital role in securing VNC connections. Implementing strong encryption protocols ensures that data transmitted between VNC clients and servers remains confidential and protected from interception. Modern VNC implementations support various encryption standards, including TLS and AES, which provide robust security features.
When configuring VNC, it is important to select the appropriate encryption method based on the level of security required. For high-security environments, using end-to-end encryption with strong cipher suites is recommended. Additionally, ensuring that encryption keys are securely stored and managed can further enhance VNC security.
VNC Attack Vectors
Brute Force Attacks
Brute force attacks are a common method used by hackers to gain unauthorized access to VNC sessions. These attacks involve systematically trying different password combinations until the correct one is found. Implementing rate-limiting and account lockout mechanisms can help mitigate the risk of brute force attacks.
Man-in-the-Middle Attacks
Man-in-the-middle (MitM) attacks occur when an attacker intercepts and potentially alters communications between VNC clients and servers. Using encrypted connections and verifying server certificates can help prevent MitM attacks and ensure the integrity of VNC sessions.
Exploiting Vulnerabilities
Software vulnerabilities in VNC clients or servers can be exploited by attackers to gain unauthorized access. Regularly updating software and applying security patches is essential for addressing these vulnerabilities and maintaining a secure VNC environment.
Best Practices for VNC Security
Adopting best practices for VNC security is crucial for protecting your systems and data. Below are some key recommendations to enhance VNC security:
- Use a firewall to restrict access to VNC ports and limit exposure to external threats.
- Implement network segmentation to isolate VNC traffic and reduce the attack surface.
- Regularly audit VNC configurations and permissions to identify and address potential security issues.
- Provide training and awareness programs for users to promote secure VNC practices.
By following these best practices, organizations can create a more secure VNC environment and minimize the risk of security breaches.
Tools for Securing VNC
Several tools and technologies are available to help secure VNC connections. These include:
- SSH Tunneling: Using SSH to tunnel VNC traffic provides an additional layer of security by encrypting communications.
- VPNs: Implementing a Virtual Private Network (VPN) ensures secure and encrypted connections for remote access.
- Security Scanners: Utilizing vulnerability scanning tools can help identify and remediate potential security weaknesses in VNC setups.
Incorporating these tools into your VNC security strategy can significantly enhance the overall security posture of your remote access infrastructure.
Real-World Case Studies
Examining real-world case studies can provide valuable insights into the importance of VNC security. For example, a 2019 incident involving a major financial institution highlighted the dangers of unsecured VNC connections. Hackers exploited vulnerabilities in the organization's VNC setup, gaining access to sensitive customer data and causing significant financial losses.
Another notable case involved a healthcare provider whose VNC system was compromised, leading to a breach of patient records. This incident underscored the critical need for robust security measures in VNC implementations, particularly in industries handling sensitive information.
Future of VNC Security
As technology continues to evolve, so too will the methods used to secure VNC connections. Emerging technologies such as quantum encryption and artificial intelligence are expected to play a significant role in enhancing VNC security in the future. Additionally, advancements in authentication protocols and threat detection systems will further bolster the security of remote access tools like VNC.
Staying informed about the latest developments in VNC security and adapting to changing threat landscapes will be essential for maintaining secure remote access capabilities in the years to come.
Conclusion and Next Steps
VNC security risk issues are a pressing concern for organizations and individuals relying on remote access tools. By understanding the potential vulnerabilities and implementing comprehensive security measures, users can effectively mitigate these risks and protect their systems and data. This article has explored various aspects of VNC security, including common risks, best practices, and tools for securing VNC connections.
To further enhance your VNC security, consider taking the following actions:
- Review and update your VNC configurations to align with best practices.
- Invest in security tools and technologies to strengthen your VNC infrastructure.
- Stay informed about the latest trends and developments in VNC security.
We invite you to share your thoughts and experiences in the comments section below. Additionally, explore other articles on our site for more insights into cybersecurity and remote access technologies. Together, we can create a safer digital environment for everyone.