Virtual Network Computing (VNC) has become an essential tool for remote desktop sharing and system administration. However, many users and organizations wonder whether VNC poses a security risk. In this article, we will explore the potential vulnerabilities associated with VNC and provide actionable strategies to mitigate these risks.
VNC is widely used across industries for remote access, troubleshooting, and collaboration. While it offers numerous advantages, understanding its security implications is crucial to protect sensitive data and systems. By implementing best practices, you can significantly reduce the risks associated with VNC usage.
Whether you're a system administrator, IT professional, or an individual using VNC for personal purposes, this guide will equip you with the knowledge and tools to ensure secure remote connections. Let's dive into the details and uncover how you can safeguard your digital environment.
Read also:Effective Method Of Ticket Sales For Gamification Summit Unlocking Success
Table of Contents:
- What is VNC?
- Is VNC Secure?
- VNC Security Risks
- Best Practices for Secure VNC Usage
- VNC Alternatives
- VNC and Compliance
- Real-World Examples of VNC Security Breaches
- Securing VNC in Organizations
- The Future of VNC Security
- Conclusion
What is VNC?
Virtual Network Computing (VNC) is a graphical desktop sharing system that allows users to remotely control another computer. It transmits the keyboard and mouse events from one computer to another, enabling real-time interaction. VNC operates over a network connection, making it an invaluable tool for remote work, technical support, and system administration.
VNC is platform-independent, meaning it can be used across different operating systems, including Windows, macOS, and Linux. This versatility has contributed to its widespread adoption in both personal and professional environments.
While VNC offers convenience and flexibility, its security features have often been questioned. Understanding the technology's core functionalities is the first step in addressing potential security concerns.
Is VNC Secure?
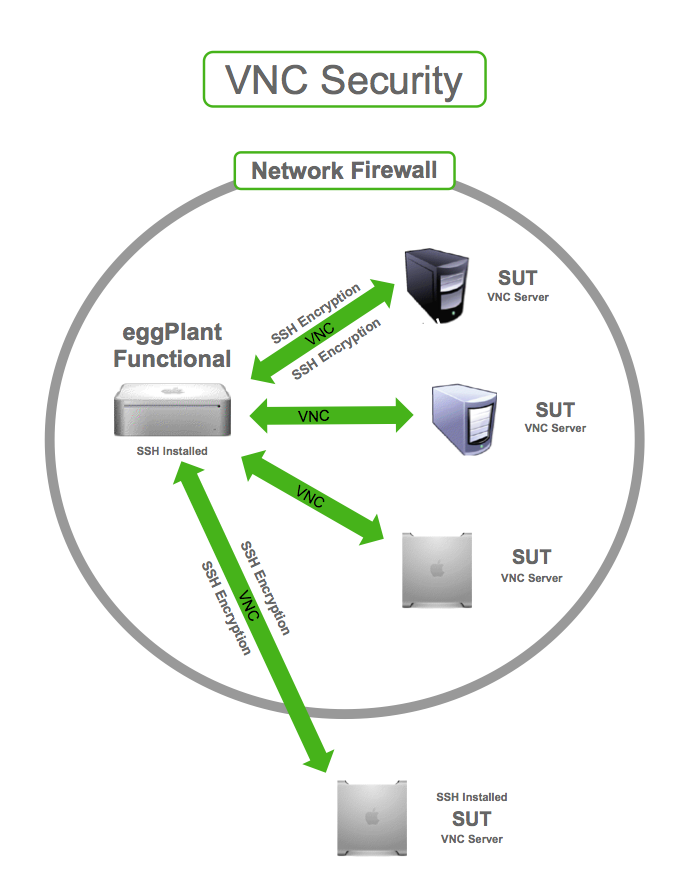
The security of VNC largely depends on how it is configured and used. By default, some VNC implementations lack robust security measures, which can expose systems to unauthorized access and data breaches. However, with proper configuration and adherence to best practices, VNC can be made secure for most use cases.
VNC security can be enhanced by implementing encryption, strong authentication mechanisms, and network segmentation. Modern VNC software versions also offer advanced features such as two-factor authentication (2FA) and firewalls, which further bolster security.
Read also:Horoscopes Mirror Unlock Your Zodiac Insights With Reflection
It is important to note that not all VNC implementations are created equal. Some open-source and commercial versions may have inherent vulnerabilities that need to be addressed through regular updates and patches.
VNC Security Risks
Despite its utility, VNC is not immune to security risks. Below are some of the most common vulnerabilities associated with VNC:
Unencrypted Connections
One of the primary risks with VNC is the lack of encryption in older versions. Unencrypted connections allow attackers to intercept sensitive data, including passwords and keystrokes, as they travel across the network. This vulnerability is particularly concerning when VNC is used over public or untrusted networks.
According to a 2020 report by cybersecurity firm Rapid7, nearly 60% of VNC installations worldwide were found to have unencrypted connections, exposing millions of devices to potential attacks.
Weak Passwords
Another significant risk factor is the use of weak or default passwords. Many users fail to configure strong authentication credentials, making it easier for attackers to gain unauthorized access to VNC-enabled systems. Brute-force attacks and password guessing are common techniques used by malicious actors to exploit weak passwords.
Industry experts recommend using complex passwords that include a mix of uppercase and lowercase letters, numbers, and special characters to mitigate this risk.
Best Practices for Secure VNC Usage
To ensure the safe and secure use of VNC, organizations and individuals should adhere to the following best practices:
Use Encryption
Enabling encryption is one of the most effective ways to secure VNC connections. Modern VNC implementations support encryption protocols such as TLS (Transport Layer Security) and SSH (Secure Shell), which protect data in transit from unauthorized access.
For example, TightVNC and UltraVNC are popular VNC software options that offer encryption features. Always verify that the VNC client and server versions you are using support encryption and configure it during setup.
Implement Strong Authentication
Strong authentication mechanisms, such as multi-factor authentication (MFA) and biometric verification, can significantly enhance VNC security. By requiring additional verification steps beyond passwords, attackers are less likely to gain unauthorized access.
Some VNC solutions integrate with third-party authentication providers, such as Google Authenticator or Microsoft Azure Active Directory, to provide an extra layer of protection.
VNC Alternatives
While VNC is a widely used remote access tool, there are several alternatives that offer enhanced security features. Below are some popular VNC alternatives:
- TeamViewer: A commercial remote desktop software that includes encryption, MFA, and session recording features.
- AnyDesk: A lightweight alternative to VNC that supports end-to-end encryption and advanced security settings.
- Remote Desktop Protocol (RDP): Microsoft's proprietary protocol for remote access, which offers robust security features when properly configured.
When selecting an alternative to VNC, consider factors such as ease of use, cost, and compatibility with your existing infrastructure.
VNC and Compliance
Organizations in regulated industries, such as healthcare and finance, must ensure that their remote access solutions comply with relevant laws and standards. For example, the Health Insurance Portability and Accountability Act (HIPAA) requires healthcare providers to implement safeguards to protect patient data.
VNC can be configured to meet compliance requirements by enabling encryption, implementing access controls, and maintaining detailed audit logs. However, it is essential to consult with legal and IT experts to ensure full compliance with applicable regulations.
Real-World Examples of VNC Security Breaches
Several high-profile VNC security breaches have highlighted the importance of securing remote access tools. In 2019, researchers discovered over 70,000 unprotected VNC servers exposed on the internet, many of which were used by healthcare and financial institutions.
Another notable incident involved a ransomware attack on a large manufacturing company, where attackers exploited a misconfigured VNC server to gain access to the organization's network. This breach resulted in significant financial losses and reputational damage.
These examples underscore the need for organizations to prioritize VNC security and adopt proactive measures to prevent similar incidents.
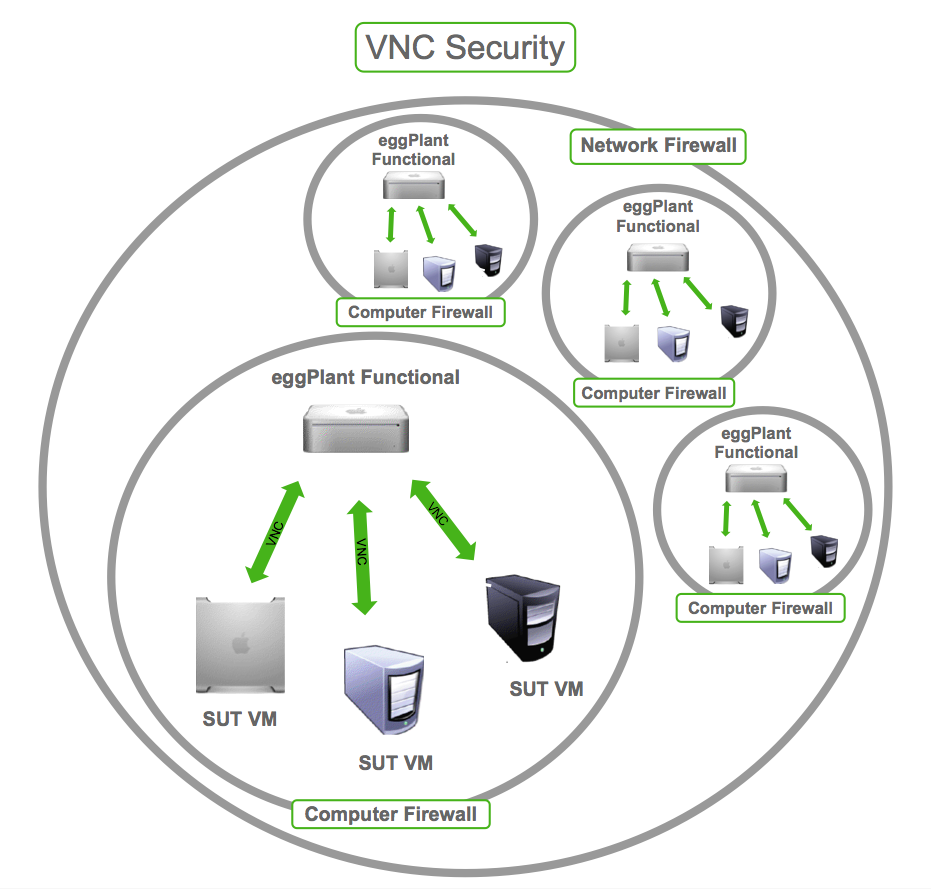
Securing VNC in Organizations
Securing VNC in an organizational setting requires a multi-layered approach that includes technical, procedural, and cultural components. Below are some strategies to enhance VNC security in organizations:
- Regular Security Audits: Conduct periodic audits to identify and address vulnerabilities in VNC configurations.
- Employee Training: Educate employees on the importance of secure remote access practices and the risks associated with VNC misuse.
- Network Segmentation: Isolate VNC-enabled systems from critical infrastructure to minimize the impact of potential breaches.
By fostering a culture of security awareness and implementing robust technical controls, organizations can effectively mitigate VNC-related risks.
The Future of VNC Security
As remote work continues to grow in popularity, the demand for secure remote access solutions like VNC will only increase. Future advancements in VNC security are likely to focus on areas such as:
- Artificial Intelligence (AI): AI-driven threat detection systems can identify and respond to suspicious VNC activities in real time.
- Quantum Encryption: Emerging quantum encryption technologies may provide unbreakable security for VNC connections in the future.
- Zero-Trust Architecture: Implementing zero-trust principles can enhance VNC security by verifying every access attempt and continuously monitoring for anomalies.
Staying informed about these advancements and adopting new security technologies will be critical for maintaining secure VNC environments in the years to come.
Conclusion
In conclusion, while VNC does pose certain security risks, these can be effectively managed through proper configuration and adherence to best practices. By understanding the potential vulnerabilities and implementing robust security measures, users and organizations can enjoy the benefits of VNC without compromising their digital security.
We encourage readers to share their thoughts and experiences with VNC security in the comments section below. Additionally, feel free to explore our other articles on cybersecurity topics for further insights and guidance. Together, we can build a safer digital world.