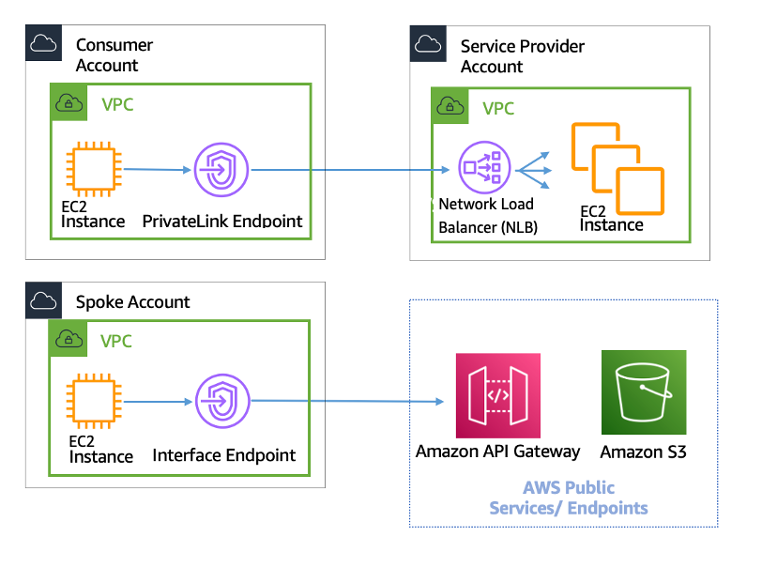
As the Internet of Things (IoT) continues to expand, securely connecting remote IoT devices to a Virtual Private Cloud (VPC) on Amazon Web Services (AWS) has become a critical concern for businesses and developers alike. The integration of IoT devices with cloud infrastructure is transforming industries, enabling smart cities, industrial automation, and advanced monitoring systems. However, ensuring secure communication between remote devices and cloud resources is paramount to protect sensitive data and maintain operational integrity.
This guide delves into the best practices for securely connecting remote IoT devices to an AWS VPC. We will explore essential configurations, tools, and strategies to enhance security while maintaining seamless connectivity. Whether you're a developer, IT professional, or decision-maker, this article will equip you with actionable insights to safeguard your IoT ecosystem.
By the end of this article, you will understand the importance of securing IoT devices in a VPC environment, the tools available in AWS to achieve this, and the steps to implement robust security measures. Let's dive in and explore how to create a secure and efficient IoT-VPC connection.
Read also:Erin Jayne Plummer The Rising Star Of Hollywood
Table of Contents
- Introduction to Secure IoT VPC Connections
- Overview of IoT and VPC on AWS
- Security Challenges in IoT-VPC Integration
- AWS Security Tools for IoT-VPC
- Best Practices for Secure IoT-VPC Connections
- Configuring the Network for IoT Devices
- Implementing Encryption for Secure Data Transfer
- Identity and Access Management (IAM) for IoT Devices
- Monitoring and Logging for Enhanced Security
- Real-World Case Studies
- Conclusion and Next Steps
Introduction to Secure IoT VPC Connections
Connecting remote IoT devices to an AWS VPC requires a thorough understanding of both IoT and cloud security principles. The AWS VPC provides a secure and isolated network environment for your IoT devices, ensuring that data transfer occurs within a controlled and monitored space. This section explains the fundamentals of IoT-VPC integration and why security is a top priority.
IoT devices are increasingly deployed in remote locations, making them vulnerable to unauthorized access and cyber threats. By leveraging AWS VPC, businesses can establish a secure network perimeter that protects IoT devices from external attacks while enabling efficient communication with cloud services.
Securing IoT devices within a VPC involves multiple layers of protection, including network segmentation, encryption, and identity management. This guide will walk you through each step, ensuring that your IoT deployment is both secure and scalable.
Overview of IoT and VPC on AWS
What is IoT?
The Internet of Things refers to the network of interconnected devices capable of collecting and exchanging data. These devices range from simple sensors to complex industrial machinery, all designed to enhance automation and efficiency.
What is AWS VPC?
An AWS Virtual Private Cloud (VPC) is a logically isolated section of the AWS cloud where you can launch your resources in a virtual network that you define. It allows you to have full control over your network configuration, including IP address ranges, subnets, route tables, and security settings.
By combining IoT with AWS VPC, businesses can create a secure and scalable environment for their IoT devices, ensuring that data is transmitted and stored safely.
Read also:Thestripesblog Tony A Comprehensive Guide To The Influential Fashion Blogger
Security Challenges in IoT-VPC Integration
Integrating IoT devices with an AWS VPC presents several security challenges that must be addressed:
- Device Authentication: Ensuring that only authorized devices can access the VPC.
- Data Encryption: Protecting data in transit and at rest from unauthorized access.
- Network Segmentation: Isolating IoT devices from other network resources to minimize attack surfaces.
- Monitoring and Logging: Detecting and responding to potential security threats in real time.
Addressing these challenges requires a comprehensive security strategy that leverages the tools and services available in AWS.
AWS Security Tools for IoT-VPC
AWS offers a robust suite of security tools designed to protect IoT devices and VPC environments. Some of the key tools include:
- AWS IoT Core: A managed cloud service that allows connected devices to interact securely with cloud applications and other devices.
- AWS Identity and Access Management (IAM): A service that helps you securely control access to AWS resources.
- Amazon CloudWatch: A monitoring and observability service that provides data and actionable insights to monitor applications, infrastructure, and network performance.
- AWS Shield: A managed Distributed Denial of Service (DDoS) protection service that safeguards web applications running on AWS.
These tools, when used together, create a multi-layered security framework that protects IoT devices and VPC resources from potential threats.
Best Practices for Secure IoT-VPC Connections
1. Use Strong Authentication Mechanisms
Implementing strong authentication mechanisms is crucial to ensuring that only authorized devices can access the VPC. AWS IoT Core provides device-specific certificates and policies that can be used to authenticate devices securely.
2. Enable End-to-End Encryption
Encrypting data both in transit and at rest is essential to protect sensitive information from unauthorized access. AWS offers several encryption services, such as AWS Key Management Service (KMS), to simplify the encryption process.
3. Segment Your Network
Network segmentation involves dividing your VPC into smaller subnets to isolate IoT devices from other network resources. This reduces the attack surface and limits the potential impact of a security breach.
4. Regularly Update Firmware and Software
Keeping IoT device firmware and software up to date is vital to addressing known vulnerabilities and ensuring that devices remain secure.
Configuring the Network for IoT Devices
Proper network configuration is essential for securely connecting IoT devices to a VPC. Key considerations include:
- Subnet Design: Create separate subnets for IoT devices to isolate them from other network resources.
- Security Groups: Use security groups to define inbound and outbound traffic rules for IoT devices.
- NAT Gateways: Implement NAT gateways to enable IoT devices to access the internet without exposing them directly to external networks.
By carefully designing your network architecture, you can create a secure and efficient environment for IoT devices.
Implementing Encryption for Secure Data Transfer
Encryption is a critical component of IoT-VPC security. AWS provides several encryption options, including:
- Transport Layer Security (TLS): Encrypts data in transit between IoT devices and the VPC.
- Server-Side Encryption (SSE): Encrypts data at rest in AWS storage services like Amazon S3.
- Customer-Managed Keys (CMK): Allows you to manage your own encryption keys using AWS KMS.
By implementing encryption at multiple levels, you can ensure that sensitive data remains protected throughout its lifecycle.
Identity and Access Management (IAM) for IoT Devices
Identity and Access Management (IAM) is a key component of IoT-VPC security. AWS IAM allows you to:
- Create and manage user accounts and permissions.
- Define policies that control access to AWS resources.
- Implement multi-factor authentication (MFA) for added security.
By leveraging IAM, you can ensure that only authorized users and devices can access your VPC and its resources.
Monitoring and Logging for Enhanced Security
Monitoring and logging are essential for detecting and responding to potential security threats. AWS provides several tools for monitoring IoT-VPC environments, including:
- Amazon CloudWatch: Collects and tracks metrics, collects and monitors log files, and responds to system-wide performance changes.
- AWS CloudTrail: Captures API calls made to AWS services and delivers log files to Amazon S3.
- AWS Shield: Protects web applications from DDoS attacks by monitoring and mitigating malicious traffic.
By regularly reviewing logs and monitoring metrics, you can quickly identify and address potential security issues.
Real-World Case Studies
Case Study 1: Smart Agriculture
Agricultural company XYZ deployed IoT sensors across its farms to monitor soil moisture, temperature, and humidity. By connecting these sensors to an AWS VPC, the company was able to securely transmit data to the cloud for analysis. Implementing encryption and network segmentation ensured that sensitive data remained protected from external threats.
Case Study 2: Industrial Automation
Manufacturing company ABC integrated IoT devices into its production lines to monitor equipment performance and optimize operations. Using AWS IoT Core and IAM, the company securely connected its devices to a VPC, enabling real-time data analysis and automated decision-making. Regular firmware updates and network monitoring further enhanced the security of the IoT ecosystem.
Conclusion and Next Steps
Securing remote IoT devices in an AWS VPC environment requires a comprehensive approach that addresses device authentication, data encryption, network segmentation, and continuous monitoring. By leveraging AWS security tools and best practices, businesses can create a secure and scalable IoT-VPC connection that protects sensitive data and ensures operational integrity.
We encourage you to take the following steps:
- Review your current IoT-VPC configuration and identify areas for improvement.
- Implement the best practices outlined in this guide to enhance security.
- Regularly monitor your IoT-VPC environment for potential threats and vulnerabilities.
Feel free to leave a comment or share this article with others who may benefit from it. For more insights on IoT and cloud security, explore our other articles and resources. Together, we can build a safer and more connected world.