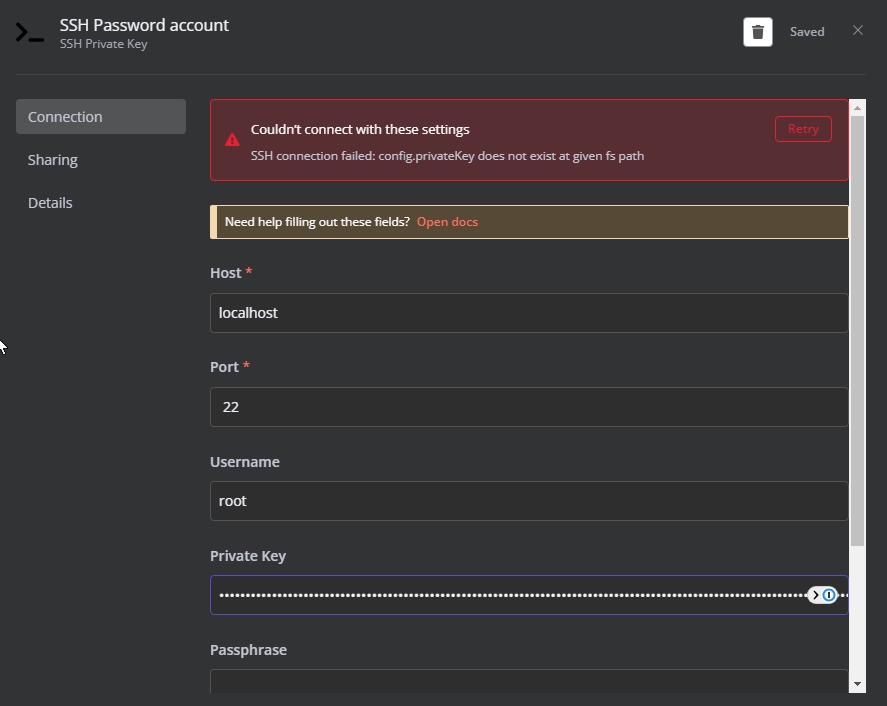
Are you struggling with the RemoteIoT platform SSH key not working issue? If yes, you're not alone. Many users face this challenge when trying to connect securely to their IoT devices using SSH keys. In this article, we'll dive deep into the causes, solutions, and best practices to resolve this problem effectively.
RemoteIoT platforms have become an integral part of modern-day connectivity, allowing seamless management of IoT devices from anywhere in the world. However, when the SSH key stops working, it can disrupt your workflow and security. Understanding the root cause is the first step toward resolving the issue.
This article aims to provide a comprehensive guide to troubleshooting and fixing the RemoteIoT platform SSH key not working problem. Whether you're a beginner or an experienced professional, you'll find valuable insights and actionable solutions to get your SSH connection back on track.
Read also:What Is A Sister Wife Relationship A Comprehensive Guide
Table of Contents
- Introduction to RemoteIoT Platform and SSH Keys
- Common Issues with RemoteIoT SSH Keys
- Troubleshooting RemoteIoT SSH Key Problems
- Fixing SSH Key Not Working Issues
- Best Practices for Managing SSH Keys
- Enhancing Security with SSH Keys
- Automating SSH Key Management
- Alternative Authentication Methods
- Frequently Asked Questions
- Conclusion and Next Steps
Introduction to RemoteIoT Platform and SSH Keys
The RemoteIoT platform enables users to manage and monitor IoT devices remotely with ease. One of the key features of this platform is its use of SSH (Secure Shell) for secure communication between devices. SSH keys play a crucial role in authenticating users and ensuring data privacy during remote connections.
SSH keys are pairs of cryptographic keys (public and private) that replace traditional password-based authentication. They provide a more secure and efficient way to access remote systems. However, when the SSH key stops working, it can lead to frustration and security concerns.
Why SSH Keys Are Essential for RemoteIoT Platforms
- Enhanced Security: SSH keys eliminate the risk of brute-force attacks that are common with password-based authentication.
- Efficiency: Users can log in to remote devices without entering a password every time.
- Scalability: SSH keys can be easily managed across multiple devices and users, making them ideal for enterprise environments.
Common Issues with RemoteIoT SSH Keys
Despite their advantages, SSH keys can sometimes fail to work as expected. Below are some of the most common issues users encounter with RemoteIoT SSH keys:
Incorrect Key Permissions
One of the primary reasons SSH keys stop working is incorrect file permissions. The private key file must have strict permissions to ensure security. If the permissions are too loose, the SSH client may refuse to use the key.
Key Mismatch
Another common issue is a mismatch between the public and private keys. If the public key on the server does not match the private key on the client, the authentication process will fail.
Server Configuration Errors
Improper server configuration can also prevent SSH keys from working. For example, if the server is not set up to accept key-based authentication, users will be unable to log in using their SSH keys.
Read also:Holly Willoughby Bath Discovering The Ultimate Relaxation Experience
Troubleshooting RemoteIoT SSH Key Problems
Troubleshooting SSH key issues requires a systematic approach. Below are some steps you can take to identify and resolve the problem:
Check Key Permissions
Ensure that the private key file has the correct permissions. Run the following command to set the appropriate permissions:
chmod 600 ~/.ssh/id_rsa
Verify Key Matching
Double-check that the public key on the server matches the private key on the client. You can use the following command to compare the keys:
ssh-keygen -lf ~/.ssh/id_rsa.pub
Review Server Configuration
Examine the server's SSH configuration file (usually located at /etc/ssh/sshd_config) to ensure that key-based authentication is enabled. Look for the following settings:
PubkeyAuthentication yesAuthorizedKeysFile .ssh/authorized_keys
Fixing SSH Key Not Working Issues
Once you've identified the problem, it's time to fix it. Below are some solutions to common SSH key issues:
Regenerate SSH Keys
If the keys are mismatched or corrupted, you may need to regenerate them. Use the following command to create a new SSH key pair:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
Update Server Configuration
If the server configuration is incorrect, update the SSH config file to enable key-based authentication. Restart the SSH service after making changes:
sudo systemctl restart ssh
Test the Connection
After implementing the fixes, test the connection to ensure that the SSH key is working properly. Use the following command:
ssh -i ~/.ssh/id_rsa user@remote-server
Best Practices for Managing SSH Keys
To avoid SSH key issues in the future, follow these best practices:
Use Strong Passphrases
Protect your private keys with strong passphrases to add an extra layer of security. Avoid using easily guessable passwords.
Limit Key Access
Restrict access to SSH keys by setting strict file permissions and storing them in secure locations.
Regularly Rotate Keys
Periodically rotate SSH keys to reduce the risk of unauthorized access. This is especially important in environments with multiple users.
Enhancing Security with SSH Keys
SSH keys are a powerful tool for securing remote connections, but they must be used correctly to maximize their effectiveness. Below are some strategies to enhance security:
Disable Password Authentication
Disable password-based authentication on your server to force users to use SSH keys. This reduces the risk of brute-force attacks.
Use Two-Factor Authentication
Combine SSH keys with two-factor authentication (2FA) for an additional layer of security. Tools like Google Authenticator can be integrated with SSH for this purpose.
Monitor Access Logs
Regularly review your server's access logs to detect and respond to unauthorized access attempts.
Automating SSH Key Management
Managing SSH keys manually can be time-consuming, especially in large-scale environments. Automating the process can save time and reduce errors. Below are some tools and techniques for automating SSH key management:
Use Configuration Management Tools
Tools like Ansible, Puppet, and Chef can automate the deployment and management of SSH keys across multiple servers.
Implement Key Rotation Policies
Create automated scripts to rotate SSH keys at regular intervals, ensuring that outdated keys are removed from the system.
Alternative Authentication Methods
While SSH keys are the most secure method of authentication, there are alternative methods you can consider:
Certificate-Based Authentication
Use X.509 certificates for authentication instead of SSH keys. This method is particularly useful in enterprise environments with centralized identity management systems.
Passwordless Authentication
Implement passwordless authentication using tools like WebAuthn or FIDO2, which rely on biometric or hardware-based authentication.
Frequently Asked Questions
Q: Why is my SSH key not working?
A: There could be several reasons, including incorrect file permissions, key mismatch, or server configuration issues. Follow the troubleshooting steps outlined in this article to identify and resolve the problem.
Q: How often should I rotate SSH keys?
A: It's recommended to rotate SSH keys every six months to one year, depending on the sensitivity of the environment and the number of users.
Q: Can I use SSH keys on multiple devices?
A: Yes, you can use the same SSH key pair on multiple devices. However, ensure that the private key is securely stored and protected with a strong passphrase.
Conclusion and Next Steps
Resolving the RemoteIoT platform SSH key not working issue requires a systematic approach to troubleshooting and fixing the problem. By following the steps and best practices outlined in this article, you can ensure that your SSH keys are secure and functioning properly.
We encourage you to share your experiences and ask questions in the comments section below. Additionally, explore other articles on our site for more insights into IoT security and remote management.
Stay connected and keep your systems secure!