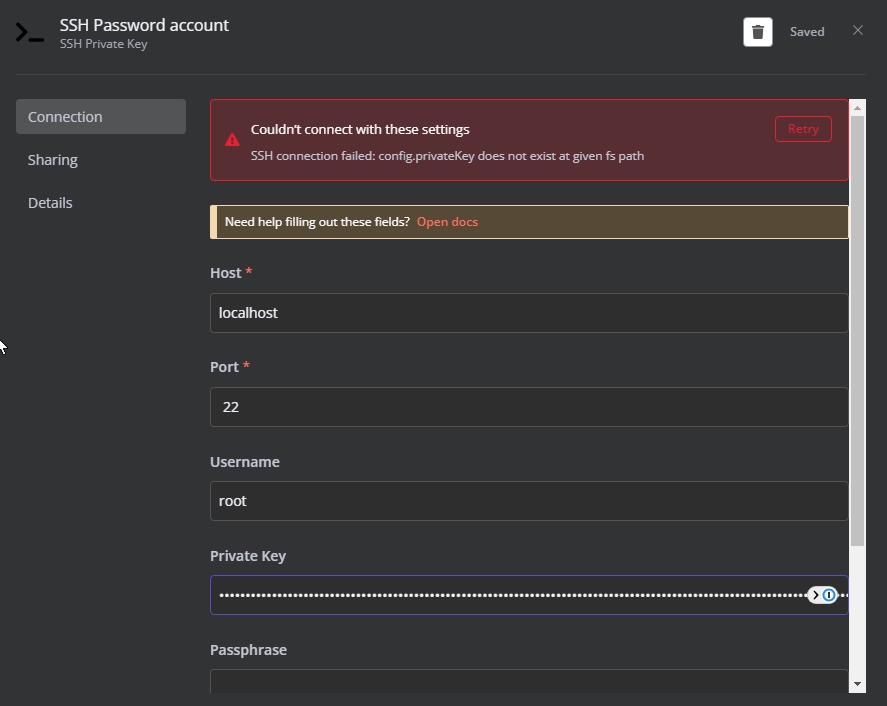
Are you experiencing issues with your RemoteIoT platform SSH key not working? If so, you're not alone. Many users encounter problems with SSH keys when trying to connect to remote servers. In this article, we will dive deep into the causes of this issue and provide actionable solutions to resolve it effectively.
SSH keys are essential for secure communication between your local machine and remote servers. However, when they fail to work, it can disrupt workflows and cause frustration. Understanding the root causes and learning how to troubleshoot them is crucial for maintaining smooth operations in your IoT environment.
This guide will walk you through everything you need to know about RemoteIoT platform SSH key issues, from identifying the problem to implementing fixes. Whether you're a beginner or an experienced developer, this article will equip you with the knowledge and tools to resolve SSH key issues efficiently.
Read also:Camila Araujo Rosa Erome Unveiling The Stars Journey Achievements And Legacy
Table of Contents
- Introduction to RemoteIoT Platform and SSH Keys
- Common Issues with RemoteIoT Platform SSH Keys
- Troubleshooting SSH Key Problems
- Regenerating SSH Keys
- File Permissions and Ownership
- Firewall and Network Configuration
- Advanced Troubleshooting Techniques
- Understanding SSH Key Authentication
- Best Practices for SSH Key Management
- Conclusion and Next Steps
Introduction to RemoteIoT Platform and SSH Keys
RemoteIoT platform is a powerful solution for managing IoT devices and applications remotely. One of the key features of this platform is its ability to securely connect to remote servers using SSH (Secure Shell) keys. SSH keys provide a secure and password-less method of authentication, ensuring that only authorized users can access the system.
However, there are instances when the RemoteIoT platform SSH key not working issue arises. This can be due to various reasons, such as misconfigured keys, permission issues, or network problems. Understanding the basics of SSH keys and how they work with the RemoteIoT platform is the first step toward resolving these issues.
In this section, we will explore the role of SSH keys in securing remote connections and their importance in maintaining the integrity of your IoT infrastructure.
Common Issues with RemoteIoT Platform SSH Keys
When dealing with SSH keys, several common issues can arise. Below are some of the most frequent problems users encounter:
- Expired or invalid SSH keys
- Incorrect file permissions on the key files
- Mismatched public and private keys
- Firewall or network restrictions blocking SSH connections
- Corrupted SSH key files
Identifying the specific issue is crucial for implementing the correct solution. In the next sections, we will discuss how to diagnose and resolve these problems effectively.
Troubleshooting SSH Key Problems
Troubleshooting SSH key issues requires a systematic approach. Here are some steps you can take to diagnose and fix the RemoteIoT platform SSH key not working problem:
Read also:Comprehensive Guide To Remoteiot Batch Job Example
Start by checking the following:
- Verify that the SSH key pair is correctly generated and added to the server.
- Ensure that the public key is correctly added to the authorized_keys file on the server.
- Check the file permissions of the SSH key files and the .ssh directory.
- Test the connection using the verbose mode (
ssh -v) to get detailed error messages.
These steps will help you pinpoint the exact cause of the issue and guide you toward the appropriate solution.
Regenerating SSH Keys
If troubleshooting fails to resolve the issue, regenerating the SSH keys may be necessary. Here's how you can create new SSH keys:
- Open a terminal or command prompt on your local machine.
- Run the following command to generate a new SSH key pair:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
Replace your_email@example.com with your actual email address. This will create a new RSA key pair with a key size of 4096 bits.
Once the keys are generated, add the public key to the server's authorized_keys file and test the connection again.
File Permissions and Ownership
Incorrect file permissions and ownership can prevent SSH keys from working properly. Here are the recommended permissions for SSH key files:
- ~/.ssh directory: 700 (drwx------)
- Private key file (id_rsa): 600 (-rw-------)
- Public key file (id_rsa.pub): 644 (-rw-r--r--)
- authorized_keys file: 600 (-rw-------)
Use the following commands to set the correct permissions:
chmod 700 ~/.ssh
chmod 600 ~/.ssh/id_rsa
chmod 644 ~/.ssh/id_rsa.pub
chmod 600 ~/.ssh/authorized_keys
Ensure that the files are owned by the correct user and group.
Firewall and Network Configuration
Firewall and network configurations can also impact SSH key functionality. Check the following:
- Ensure that the SSH port (default is 22) is open on the server's firewall.
- Verify that there are no network restrictions blocking SSH connections.
- Test the connection from a different network to rule out local network issues.
Consult your network administrator if you suspect a firewall or network-related problem.
Advanced Troubleshooting Techniques
For more advanced troubleshooting, consider the following techniques:
- Check the server's SSH logs for error messages. These logs are typically located in
/var/log/auth.logon Linux systems. - Use the
ssh -vvvcommand to enable maximum verbosity and gather detailed information about the connection process. - Test the connection with a different SSH client to rule out client-side issues.
These techniques can provide deeper insights into the root cause of the issue.
Understanding SSH Key Authentication
SSH key authentication is a secure method of authenticating users without the need for passwords. It works by generating a pair of cryptographic keys: a public key and a private key. The public key is stored on the server, while the private key remains on the client machine.
When a user attempts to connect to the server, the SSH client sends a signature generated using the private key. The server verifies this signature using the public key, ensuring that the user is authorized to access the system.
Understanding this process can help you troubleshoot and resolve SSH key issues more effectively.
Best Practices for SSH Key Management
Managing SSH keys effectively is essential for maintaining the security of your RemoteIoT platform. Here are some best practices to follow:
- Use strong, unique passwords for protecting your private keys.
- Regularly rotate SSH keys to minimize the risk of compromise.
- Limit the number of users with access to the server's SSH keys.
- Monitor SSH key usage and revoke keys that are no longer needed.
- Use SSH key agents like ssh-agent or Keychain to manage keys securely.
By following these best practices, you can enhance the security of your RemoteIoT platform and reduce the likelihood of SSH key-related issues.
Conclusion and Next Steps
In conclusion, the RemoteIoT platform SSH key not working issue can be resolved by systematically diagnosing and addressing the underlying causes. From troubleshooting common problems to implementing best practices for SSH key management, this guide has provided you with the tools and knowledge to handle these challenges effectively.
We encourage you to apply the solutions and techniques discussed in this article to resolve your SSH key issues. If you found this article helpful, please consider sharing it with others who may benefit from it. Additionally, feel free to leave a comment below with any questions or feedback.
For further reading, explore our other articles on IoT security and remote server management. Stay updated with the latest trends and technologies in the world of IoT and cybersecurity.