In today's interconnected world, remote desktop tools like VNC Viewer have become indispensable for remote work and IT management. However, as organizations and individuals increasingly rely on VNC Viewer, they also expose themselves to potential security risks. Understanding these risks and implementing robust security measures is critical to protect sensitive data and systems.
VNC Viewer, short for Virtual Network Computing Viewer, allows users to remotely access and control computers over a network. While this technology offers numerous advantages, such as increased productivity and flexibility, it also comes with inherent vulnerabilities that malicious actors can exploit. As cyber threats continue to evolve, staying informed about these risks is more important than ever.
This article delves into the security risks associated with VNC Viewer, exploring potential vulnerabilities, best practices for mitigating these risks, and actionable strategies to safeguard your systems. By the end, you'll have a comprehensive understanding of how to use VNC Viewer securely and confidently.
Read also:Hoka Cosmic Pearl Bondi 8 The Ultimate Guide To Comfort And Performance
Table of Contents
- Introduction to VNC Viewer Security Risks
- How VNC Viewer Works
- Common Security Risks in VNC Viewer
- Authentication Vulnerabilities
- Encryption Weaknesses
- Malware and Exploits
- Best Practices for Securing VNC Viewer
- Using Firewalls to Enhance Security
- Keeping Software Updated
- Conclusion and Call to Action
Introduction to VNC Viewer Security Risks
VNC Viewer is a powerful tool that enables remote access to computers, allowing users to control them as if they were sitting in front of the machine. However, this convenience comes with a price—security risks that can compromise sensitive data and systems. As cybercriminals become more sophisticated, understanding and addressing these risks is crucial for maintaining a secure environment.
How VNC Viewer Works
VNC Viewer operates by transmitting keyboard and mouse inputs from one computer to another over a network connection. It uses the RFB (Remote Framebuffer) protocol to send screen updates between the client and server, enabling real-time interaction. While this process is efficient and effective, it also creates opportunities for attackers to intercept or manipulate the data being transmitted.
Key Features of VNC Viewer
- Remote desktop access
- Real-time interaction
- Platform compatibility
- Customizable settings
Common Security Risks in VNC Viewer
Several security risks are associated with VNC Viewer, ranging from weak authentication protocols to unsecured connections. Below are some of the most common risks:
- Weak passwords
- Lack of encryption
- Unpatched vulnerabilities
- Malware infections
Impact of Security Risks
These risks can lead to data breaches, unauthorized access, and even complete system compromise. Organizations that fail to address these vulnerabilities put themselves at significant risk of financial loss and reputational damage.
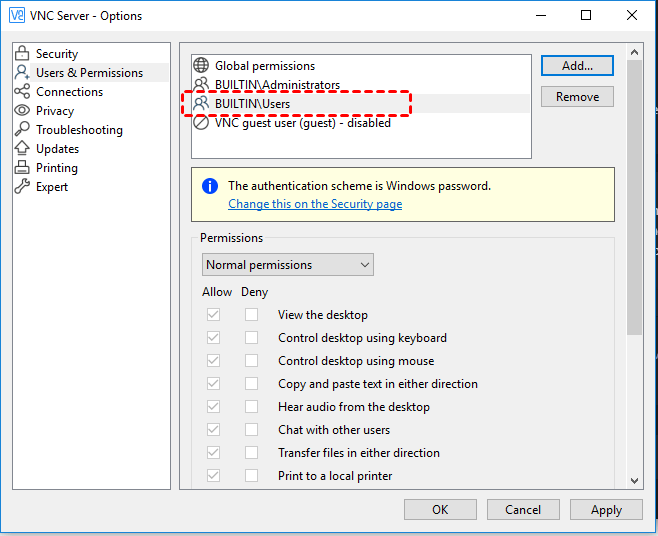
Authentication Vulnerabilities
One of the primary security concerns with VNC Viewer is weak authentication mechanisms. Many users rely on simple passwords or fail to enable two-factor authentication (2FA), making it easier for attackers to gain unauthorized access.
Best Practices for Authentication
- Use strong, unique passwords
- Enable two-factor authentication
- Limit login attempts
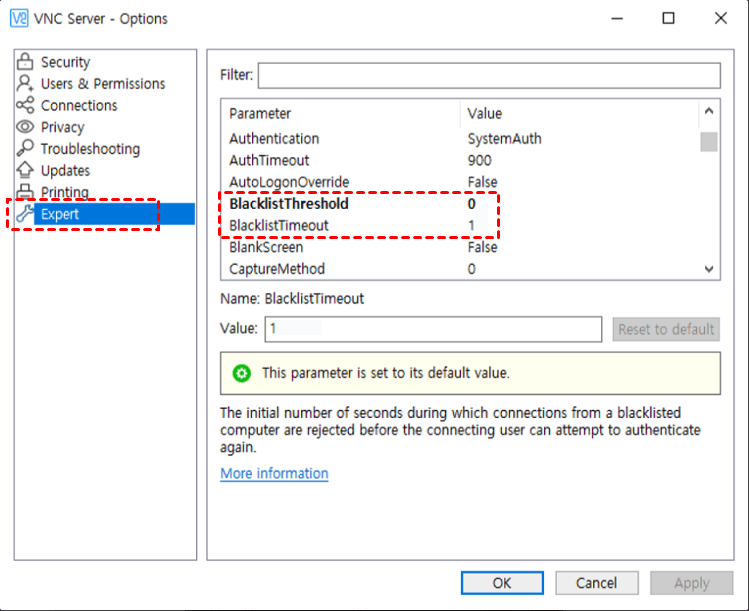
Encryption Weaknesses
Encryption is critical for securing data transmitted over VNC Viewer. However, older versions of VNC may use outdated encryption protocols that are vulnerable to attacks. Ensuring that the latest encryption standards are in place is essential for protecting sensitive information.
Read also:Rebekah Vardy And Peter Andre The Untold Story Of Fame Influence And Relationships
Implementing Strong Encryption
- Use AES encryption
- Regularly update encryption protocols
- Avoid using legacy encryption methods
Malware and Exploits
VNC Viewer can also be a vector for malware and other malicious software. Attackers may exploit vulnerabilities in the software to install malware on target systems, leading to data theft or system compromise.
Protecting Against Malware
- Install reputable antivirus software
- Regularly scan for malware
- Keep all software up to date
Best Practices for Securing VNC Viewer
Securing VNC Viewer requires a multi-layered approach that addresses both technical and procedural vulnerabilities. Below are some best practices to help you protect your systems:
Technical Best Practices
- Use secure connections (e.g., SSH tunneling)
- Enable firewall rules to restrict access
- Regularly audit system logs
Procedural Best Practices
- Train employees on cybersecurity awareness
- Limit VNC access to authorized personnel
- Conduct regular security assessments
Using Firewalls to Enhance Security
Firewalls play a critical role in securing VNC Viewer by controlling inbound and outbound traffic. By configuring firewall rules to restrict access to VNC ports, organizations can significantly reduce the risk of unauthorized access.
Configuring Firewall Rules
- Allow only trusted IP addresses
- Block unnecessary ports
- Monitor traffic logs for suspicious activity
Keeping Software Updated
Keeping VNC Viewer and related software up to date is essential for maintaining security. Software updates often include patches for known vulnerabilities, ensuring that your systems remain protected against the latest threats.
Importance of Regular Updates
- Fixes for security vulnerabilities
- Improved performance and stability
- Access to new features
Conclusion and Call to Action
VNC Viewer is a valuable tool for remote work and IT management, but its security risks must not be overlooked. By understanding these risks and implementing the best practices outlined in this article, you can significantly enhance the security of your VNC connections and protect your systems from potential threats.
We encourage you to take action by reviewing your current VNC setup, implementing stronger authentication measures, and ensuring that all software is up to date. Your feedback and questions are also valuable—please leave a comment below or share this article with others who may benefit from it. Together, we can create a safer digital environment.
For further reading, explore our other articles on cybersecurity and remote work solutions. Stay informed, stay secure!