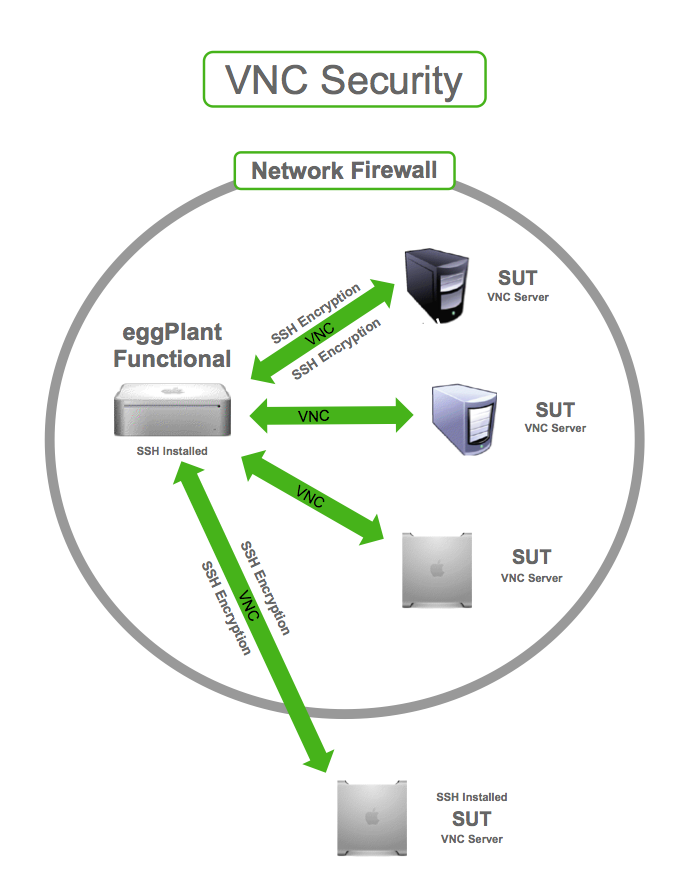
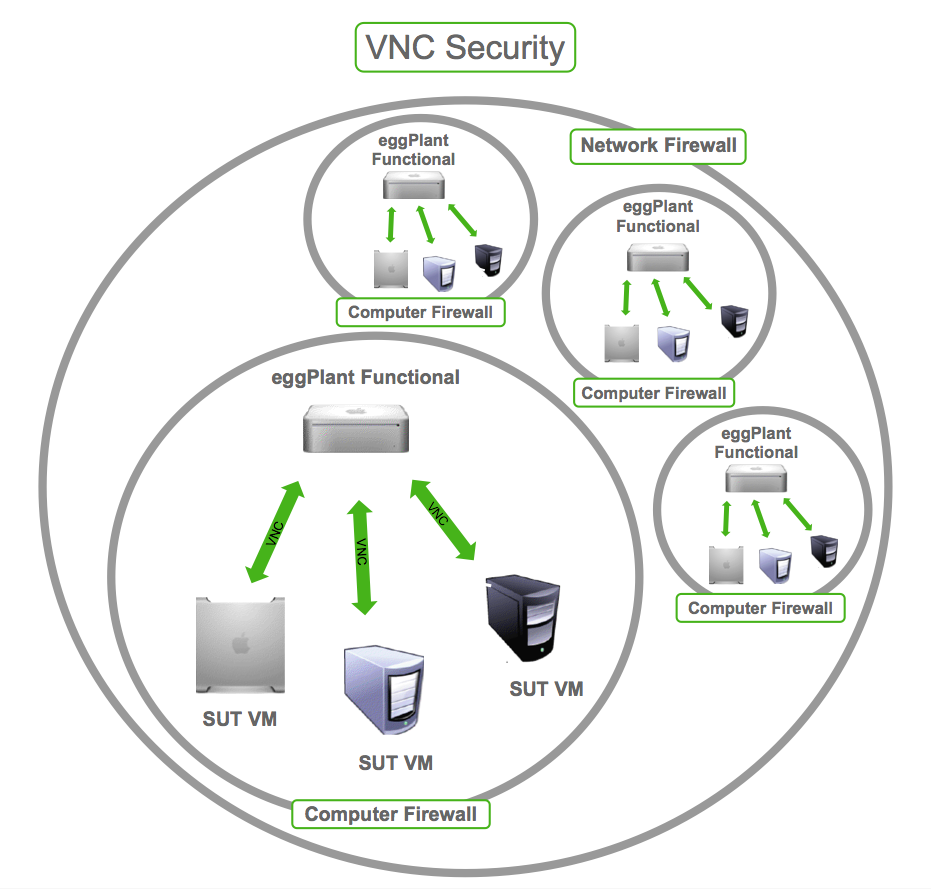
Virtual Network Computing (VNC) has become a popular tool for remote desktop access, enabling users to control computers from remote locations. However, VNC security holes have emerged as a critical concern for organizations and individuals alike. Understanding these vulnerabilities is essential to protect sensitive data and maintain secure connections. In this article, we will explore the risks associated with VNC, discuss the most common security holes, and provide actionable steps to mitigate these threats.
As remote work continues to grow, the demand for VNC technology has skyrocketed. While it offers convenience and efficiency, the security risks cannot be ignored. Cybercriminals are constantly searching for vulnerabilities in VNC systems to exploit, putting users' data and privacy at risk.
In this comprehensive guide, we will delve into the world of VNC security, exploring the potential dangers and offering practical solutions to safeguard your remote connections. Whether you're an IT professional or a casual user, this article will equip you with the knowledge and tools to enhance your VNC security.
Read also:Russell Grant Daily Horoscope Your Ultimate Guide To Understanding Your Zodiac Destiny
Table of Contents
- Introduction to VNC Security
- Common VNC Security Vulnerabilities
- Bi-directional Access Risks
- Authentication Flaws
- Encryption Issues
- Data Leakage and Exposure
- Types of VNC Attacks
- Mitigation Strategies
- Best Practices for VNC Security
- Future Trends in VNC Security
Introduction to VNC Security
VNC, or Virtual Network Computing, is a graphical desktop-sharing system that allows users to remotely control another computer. It transmits keyboard and mouse events from one computer to another over the network, enabling real-time interaction. While VNC is a powerful tool, it is not without its security challenges.
VNC security holes can lead to unauthorized access, data breaches, and other cyber threats. These vulnerabilities often arise from improper configuration, weak authentication mechanisms, and insufficient encryption. As a result, organizations must prioritize securing their VNC connections to protect sensitive information.
In this section, we will examine the basics of VNC and its role in remote access, highlighting the importance of addressing security concerns.
Common VNC Security Vulnerabilities
Weak Passwords
One of the most prevalent VNC security holes is the use of weak passwords. Many users opt for simple, easily guessable passwords, making it easier for attackers to gain unauthorized access. To mitigate this risk, it is crucial to implement strong password policies and enforce multi-factor authentication (MFA).
Outdated Software
Using outdated VNC software can expose systems to known vulnerabilities. Regularly updating VNC clients and servers ensures that the latest security patches are applied, reducing the risk of exploitation.
Unsecured Networks
Connecting to VNC over unsecured networks, such as public Wi-Fi, can leave users vulnerable to man-in-the-middle (MITM) attacks. It is essential to use secure, encrypted connections to prevent eavesdropping and data interception.
Read also:Holly Willoughby Bath Discovering The Ultimate Relaxation Experience
Bi-directional Access Risks
VNC allows bi-directional access, meaning users can control both the local and remote systems simultaneously. While this feature enhances usability, it also introduces security risks. If a malicious actor gains access to one system, they may be able to compromise the other, leading to cascading security breaches.
To address this issue, organizations should implement strict access controls and monitor VNC sessions for suspicious activity.
Authentication Flaws
Single-Factor Authentication
Relying solely on single-factor authentication (passwords) is a significant VNC security hole. Attackers can exploit weak or stolen credentials to gain unauthorized access. Implementing multi-factor authentication adds an extra layer of security, making it more difficult for attackers to breach systems.
Default Credentials
Using default usernames and passwords provided by VNC software manufacturers is another common mistake. Attackers can easily find these credentials online and use them to infiltrate systems. Always change default credentials immediately after installation.
Encryption Issues
Encryption is critical for securing VNC connections, but many implementations suffer from encryption-related vulnerabilities. Some VNC clients and servers use outdated encryption protocols, which can be easily cracked by modern cybercriminals.
To enhance encryption, users should opt for modern protocols such as TLS (Transport Layer Security) and ensure that encryption keys are securely managed.
Data Leakage and Exposure
VNC security holes can lead to data leakage and exposure, compromising sensitive information. Attackers may intercept data transmitted over unsecured VNC connections or exploit vulnerabilities to access stored data on remote systems.
Implementing robust data protection measures, such as data encryption and access controls, can help mitigate these risks. Regularly auditing VNC systems for vulnerabilities is also essential to maintaining data integrity.
Types of VNC Attacks
Brute Force Attacks
Brute force attacks involve systematically trying different password combinations until the correct one is found. Attackers often target VNC systems with weak passwords or no password protection. Implementing account lockout policies and rate-limiting can help prevent brute force attacks.
Man-in-the-Middle Attacks
Man-in-the-middle (MITM) attacks occur when attackers intercept and manipulate data transmitted between VNC clients and servers. Using secure, encrypted connections and verifying server certificates can help prevent MITM attacks.
Malware Injection
Malicious actors may use compromised VNC connections to inject malware into target systems. Ensuring that VNC clients and servers are up-to-date and implementing endpoint protection solutions can help mitigate this risk.
Mitigation Strategies
Addressing VNC security holes requires a multi-faceted approach. Below are some effective strategies for mitigating VNC-related risks:
- Implement strong password policies and enforce multi-factor authentication.
- Regularly update VNC software to address known vulnerabilities.
- Use secure, encrypted connections (e.g., TLS) for all VNC communications.
- Restrict VNC access to trusted networks and IP addresses.
- Monitor VNC sessions for suspicious activity and investigate anomalies promptly.
Best Practices for VNC Security
Regular Audits
Conducting regular security audits of VNC systems is essential for identifying and addressing vulnerabilities. These audits should include reviewing access controls, encryption settings, and system logs for signs of unauthorized access.
User Training
Training users on VNC security best practices can significantly reduce the risk of human error. Educate employees on the importance of strong passwords, secure connections, and recognizing phishing attempts.
Incident Response Planning
Developing an incident response plan for VNC-related security incidents ensures that organizations can respond quickly and effectively to breaches. This plan should include procedures for isolating compromised systems, notifying affected parties, and restoring normal operations.
Future Trends in VNC Security
As technology continues to evolve, so too will the landscape of VNC security. Emerging trends such as artificial intelligence (AI) and machine learning (ML) are expected to play a significant role in enhancing VNC security by detecting and responding to threats in real-time.
Additionally, the adoption of zero-trust architecture and advanced encryption protocols will further strengthen VNC security, protecting users from increasingly sophisticated cyber threats.
Conclusion
VNC security holes pose a significant risk to organizations and individuals who rely on remote access technology. By understanding the vulnerabilities and implementing effective mitigation strategies, users can enhance their VNC security and protect sensitive data.
We encourage readers to take action by reviewing their VNC configurations, updating software, and adopting best practices for secure remote access. Feel free to share this article with colleagues and leave a comment below if you have any questions or additional tips for improving VNC security.
Data Source: CISA