In today's hyper-connected world, secure IoT platform has become an essential need for businesses and individuals alike. As more devices get connected to the internet, the importance of securing them cannot be overstated. A secure IoT platform ensures that your devices are protected from cyber threats and unauthorized access.
The Internet of Things (IoT) has revolutionized the way we interact with technology. However, as the number of connected devices continues to grow, so does the risk of cyberattacks. This is where a secure IoT platform comes into play. It acts as a shield, safeguarding your devices and data from potential threats.
This comprehensive guide will delve into the intricacies of secure IoT platforms, explaining their significance, functionality, and best practices for implementation. By the end of this article, you will have a clear understanding of how to protect your IoT ecosystem effectively.
Read also:Devil Jin Tekken 8 Customization A Comprehensive Guide For Fans
Table of Contents
- Introduction to Secure IoT Platform
- Why Secure IoT Platforms Are Critical
- Secure IoT Platform Architecture
- Key Security Features of IoT Platforms
- Challenges in Securing IoT Platforms
- Best Practices for Securing IoT Platforms
- Real-World Use Cases of Secure IoT Platforms
- Data Protection in IoT Platforms
- Emerging Technologies in IoT Security
- The Future of Secure IoT Platforms
Introduction to Secure IoT Platform
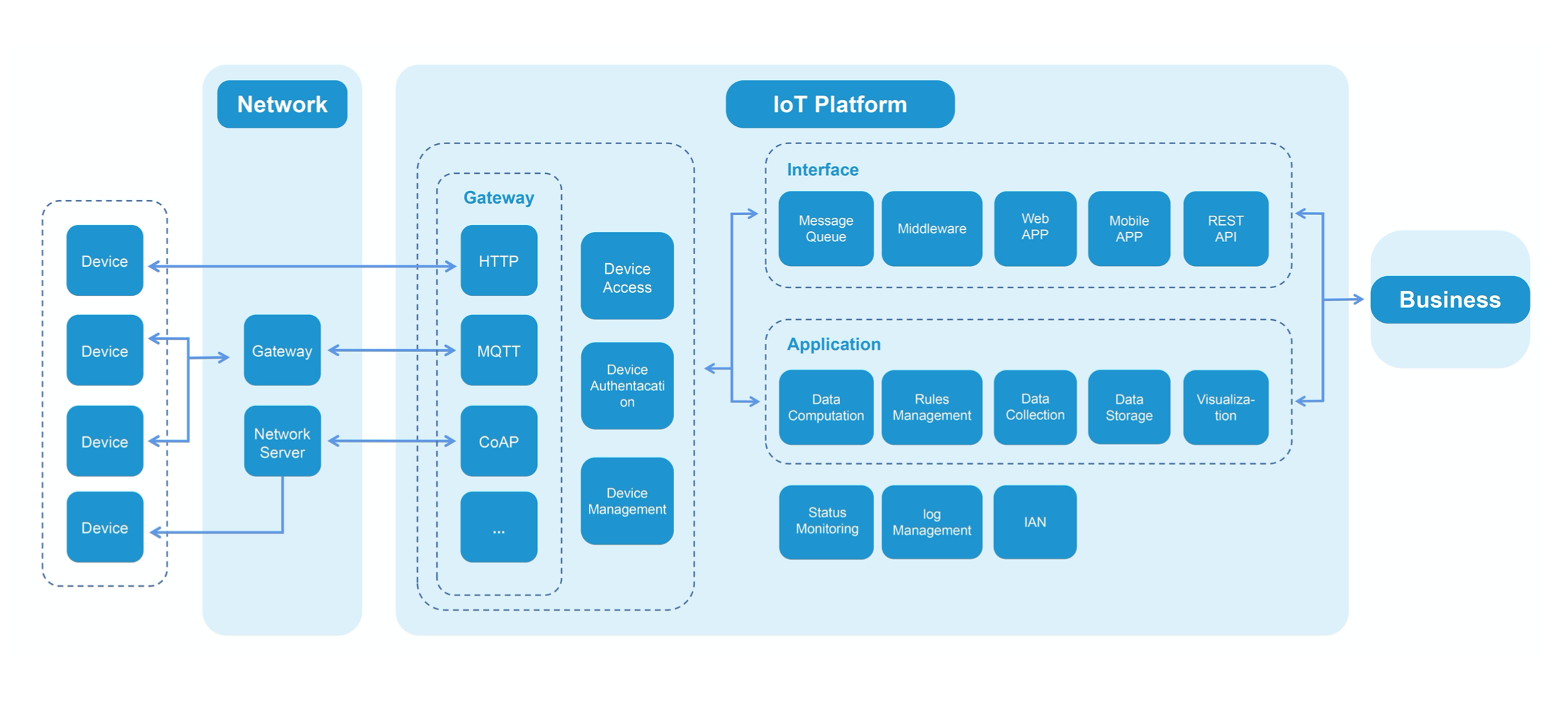
The concept of a secure IoT platform revolves around creating a robust framework to safeguard connected devices. These platforms are designed to address the vulnerabilities inherent in IoT ecosystems. By integrating advanced security protocols, secure IoT platforms ensure that data transmission, device authentication, and network communication remain protected.
How IoT Platforms Work
IoT platforms function as intermediaries between connected devices and the cloud. They facilitate data collection, processing, and analysis while ensuring that security measures are in place. A secure IoT platform typically includes components such as device management, data encryption, and access control.
Importance of Security in IoT
With billions of devices connected to the internet, the risk of cyberattacks is significant. A secure IoT platform mitigates these risks by implementing end-to-end encryption, secure authentication mechanisms, and regular firmware updates. These measures help prevent unauthorized access and data breaches.
Why Secure IoT Platforms Are Critical
Secure IoT platforms are crucial for maintaining the integrity and confidentiality of data. Without proper security measures, IoT devices can become easy targets for hackers. This section explores the reasons why securing IoT platforms is essential.
Preventing Cyberattacks
Cyberattacks on IoT devices have increased dramatically in recent years. Hackers exploit vulnerabilities in unsecured platforms to gain access to sensitive information. A secure IoT platform minimizes these risks by implementing robust security protocols.
Protecting User Privacy
User privacy is a top priority in the IoT ecosystem. Secure platforms ensure that personal data collected by devices remains confidential and is not misused. This builds trust between consumers and service providers.
Read also:Bruno Mars Twin Exploring The Fascinating Connection Between The Superstar And His Lookalike
Secure IoT Platform Architecture
The architecture of a secure IoT platform is designed to handle the complexities of IoT security. It consists of multiple layers, each responsible for a specific function. This section breaks down the architecture of secure IoT platforms.
Device Layer
The device layer includes all connected devices in the IoT ecosystem. These devices are equipped with sensors and actuators that collect and transmit data. A secure IoT platform ensures that each device is authenticated and authorized before connecting to the network.
Network Layer
The network layer facilitates communication between devices and the cloud. It uses secure protocols such as TLS and SSL to encrypt data during transmission. This ensures that data remains protected from interception and tampering.
Application Layer
The application layer provides users with a user-friendly interface to interact with IoT devices. It also includes analytics tools that process and analyze data collected by devices. A secure IoT platform ensures that application-layer security is maintained through role-based access control and secure APIs.
Key Security Features of IoT Platforms
Secure IoT platforms come equipped with a range of security features designed to protect devices and data. This section highlights some of the key security features of these platforms.
- End-to-End Encryption: Ensures that data is encrypted during transmission and storage.
- Device Authentication: Verifies the identity of connected devices to prevent unauthorized access.
- Access Control: Implements role-based access control to restrict access to sensitive data.
- Firmware Updates: Provides regular firmware updates to patch security vulnerabilities.
Challenges in Securing IoT Platforms
Despite the advancements in IoT security, several challenges remain. This section discusses the challenges faced in securing IoT platforms and potential solutions.
Scalability Issues
As the number of connected devices grows, securing IoT platforms becomes increasingly challenging. Scalability issues can lead to performance degradation and security vulnerabilities. To address this, platforms must be designed to handle large-scale deployments efficiently.
Interoperability Problems
Different IoT devices often use different communication protocols, making interoperability a challenge. Secure IoT platforms must support multiple protocols to ensure seamless integration of devices.
Best Practices for Securing IoT Platforms
Implementing best practices is essential for securing IoT platforms. This section outlines some of the best practices that organizations can follow.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities in IoT platforms. Organizations should perform audits periodically to ensure that their platforms remain secure.
Employee Training
Training employees on IoT security best practices is crucial. Employees should be aware of potential threats and know how to respond to security incidents effectively.
Real-World Use Cases of Secure IoT Platforms
Secure IoT platforms have been successfully implemented in various industries. This section explores some real-world use cases of these platforms.
Smart Homes
Secure IoT platforms are widely used in smart homes to protect connected devices such as smart thermostats, security cameras, and lighting systems. These platforms ensure that user data remains secure and devices function optimally.
Industrial IoT
In the industrial sector, secure IoT platforms are used to monitor and control machinery. They help prevent downtime and improve operational efficiency while maintaining security.
Data Protection in IoT Platforms
Data protection is a critical aspect of secure IoT platforms. This section discusses how these platforms protect user data and comply with regulations.
Compliance with Regulations
Secure IoT platforms adhere to data protection regulations such as GDPR and CCPA. They ensure that user data is collected, stored, and processed in compliance with these regulations.
Data Encryption
Data encryption is a key feature of secure IoT platforms. It ensures that data remains confidential during transmission and storage, preventing unauthorized access.
Emerging Technologies in IoT Security
The field of IoT security is constantly evolving, with new technologies emerging to address existing challenges. This section highlights some of the emerging technologies in IoT security.
Blockchain Technology
Blockchain technology is being explored for its potential to enhance IoT security. It provides a decentralized and tamper-proof ledger for storing device data, ensuring its integrity.
Artificial Intelligence
Artificial intelligence (AI) is being used to detect and respond to security threats in real-time. AI-powered platforms can analyze vast amounts of data to identify anomalies and potential threats.
The Future of Secure IoT Platforms
The future of secure IoT platforms looks promising, with advancements in technology driving innovation. This section discusses the future trends in IoT security.
Increased Adoption of AI
As AI technology advances, its adoption in IoT security is expected to increase. AI will play a crucial role in automating security processes and improving threat detection.
Integration of Emerging Technologies
Secure IoT platforms will integrate emerging technologies such as blockchain and quantum cryptography to enhance security. These technologies will provide robust solutions to existing security challenges.
Conclusion
In conclusion, secure IoT platforms are vital for protecting connected devices and data. They provide a comprehensive framework for addressing the security challenges in IoT ecosystems. By implementing best practices and leveraging emerging technologies, organizations can ensure that their IoT platforms remain secure and efficient.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into IoT security and related topics.