Remote access behind router has become a critical aspect of modern networking, enabling users to securely connect to their home or office networks from anywhere in the world. As remote work and global connectivity continue to grow, understanding how to set up and maintain secure remote access through a router is essential for both individuals and businesses.
With the increasing reliance on digital tools, the ability to access your network remotely allows you to retrieve files, manage devices, and monitor security systems without being physically present. However, configuring remote access behind a router requires careful planning and implementation to ensure security and functionality.
This article delves into the intricacies of remote access behind router, offering step-by-step guidance, expert advice, and practical tips to help you set up a secure and reliable connection. Whether you're a tech enthusiast or a small business owner, this guide will equip you with the knowledge you need to navigate the complexities of remote networking.
Read also:Kyren Wilson Family A Comprehensive Look Into The Life Of The Snooker Sensation
Table of Contents
- Introduction to Remote Access Behind Router
- Why Is Remote Access Important?
- How Remote Access Works
- Types of Remote Access
- Setting Up Remote Access Behind Router
- Securing Your Remote Access
- Troubleshooting Common Issues
- Tools and Software for Remote Access
- Best Practices for Remote Access
- The Future of Remote Access
Introduction to Remote Access Behind Router
Remote access behind router refers to the ability to connect to a private network from an external location, even when the network is protected by a router's firewall. This setup is essential for remote work, file sharing, and managing IoT devices from afar. The process involves configuring port forwarding, setting up a dynamic DNS service, and ensuring proper network security.
Understanding the basics of remote access is crucial for anyone looking to enhance their networking capabilities. Whether you're accessing files on your home computer or monitoring your office security cameras, the principles remain the same. By following best practices and utilizing the right tools, you can establish a seamless connection that meets your needs.
Why Is Remote Access Important?
Remote access has transformed the way we work and interact with technology. It provides flexibility, improves productivity, and allows for better resource management. For businesses, remote access enables employees to collaborate on projects, access company databases, and perform tasks as if they were physically present in the office.
On a personal level, remote access allows you to control smart home devices, retrieve important files, and monitor security systems. This convenience is especially valuable in today's fast-paced world, where being connected is almost a necessity.
Key Benefits of Remote Access
- Increased Productivity: Employees can work from anywhere without compromising efficiency.
- Cost Savings: Reduces the need for physical office space and travel expenses.
- Improved Security: Enables real-time monitoring of networks and devices.
- Flexibility: Provides access to resources from any location with an internet connection.
How Remote Access Works
Remote access behind router operates by creating a secure connection between your device and the target network. This involves several key components:
- Port Forwarding: Directs incoming traffic to the correct device within the network.
- Dynamic DNS (DDNS): Maps your router's IP address to a memorable domain name.
- Encryption: Protects data transmitted between devices from unauthorized access.
- Authentication: Ensures only authorized users can access the network.
When you initiate a remote connection, your device sends a request to the router, which then forwards the request to the appropriate device on the network. This process is transparent to the user but requires proper configuration to function correctly.
Read also:Hoka Cosmic Pearl Bondi 8 The Ultimate Guide To Comfort And Performance
Types of Remote Access
There are several methods for achieving remote access behind router, each with its own advantages and limitations. The most common types include:
1. SSH (Secure Shell)
SSH is a protocol used for secure communication between devices. It provides encryption and authentication, making it ideal for remote administration tasks.
2. RDP (Remote Desktop Protocol)
RDP allows users to remotely control a computer's desktop interface. It is widely used in corporate environments for remote work and troubleshooting.
3. VPN (Virtual Private Network)
A VPN creates a secure tunnel between your device and the target network, enabling encrypted communication and protecting sensitive data.
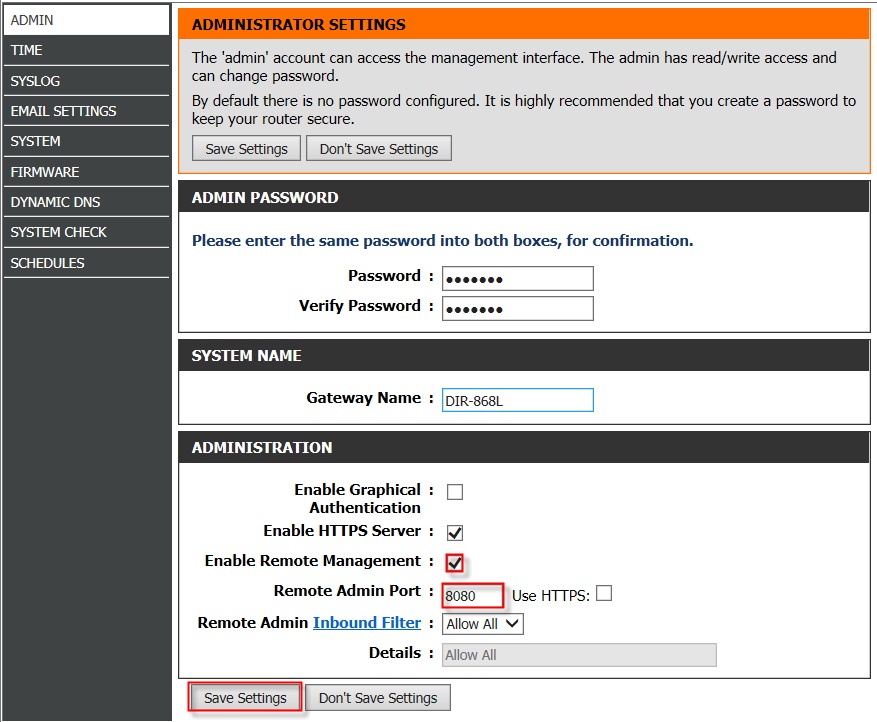
Setting Up Remote Access Behind Router
Configuring remote access behind router involves several steps. Below is a step-by-step guide to help you set up a secure connection:
Step 1: Enable Port Forwarding
Port forwarding directs incoming traffic to the correct device within your network. To enable port forwarding:
- Log in to your router's admin interface.
- Navigate to the "Port Forwarding" or "NAT" settings.
- Specify the port number and the IP address of the target device.
- Save the changes and restart the router if necessary.
Step 2: Set Up Dynamic DNS
Dynamic DNS (DDNS) maps your router's IP address to a domain name, making it easier to connect. To set up DDNS:
- Choose a DDNS provider and create an account.
- Register a domain name with the provider.
- Configure your router to update the DDNS service with your current IP address.
Step 3: Configure Firewall Settings
Your router's firewall protects your network from unauthorized access. To allow remote access:
- Identify the ports required for your chosen protocol (e.g., SSH uses port 22, RDP uses port 3389).
- Open these ports in the firewall settings.
- Ensure only necessary ports are open to minimize security risks.
Securing Your Remote Access
Security is paramount when setting up remote access behind router. Follow these best practices to protect your network:
- Use Strong Passwords: Implement complex passwords and enable two-factor authentication (2FA).
- Encrypt Data: Use protocols like SSH or SSL/TLS to encrypt data transmissions.
- Regularly Update Firmware: Keep your router and devices up to date with the latest security patches.
- Monitor Activity: Track login attempts and investigate any suspicious activity.
Troubleshooting Common Issues
Even with proper configuration, issues may arise when setting up remote access behind router. Below are some common problems and their solutions:
1. Connection Refused
If you receive a "connection refused" error, ensure that:
- The correct port is forwarded in your router settings.
- The target device is powered on and connected to the network.
- Firewall rules allow traffic on the specified port.
2. IP Address Changes
If your router's IP address changes, update the DDNS service with the new address. Alternatively, consider using a static IP address if available.
Tools and Software for Remote Access
Several tools and software solutions can simplify the process of remote access behind router:
1. TeamViewer
TeamViewer is a popular remote access tool that requires no complex configuration. It provides cross-platform support and advanced security features.
2. AnyDesk
AnyDesk offers fast and secure remote connections with low latency. It is suitable for both personal and business use.
3. Windows Remote Desktop
Windows Remote Desktop is a built-in feature of Windows that allows users to connect to remote computers using RDP.
Best Practices for Remote Access
To ensure a smooth and secure remote access experience, follow these best practices:
- Limit Access: Restrict remote access to essential personnel only.
- Regularly Audit: Periodically review access logs and permissions.
- Backup Data: Maintain regular backups of critical files and databases.
- Stay Informed: Stay updated on the latest security threats and solutions.
The Future of Remote Access
As technology continues to evolve, remote access behind router will become even more sophisticated and secure. Advancements in AI, machine learning, and quantum encryption will enhance the capabilities of remote networking tools, providing users with faster and more reliable connections.
The increasing adoption of cloud computing and edge devices will further transform the landscape of remote access. Businesses will rely more heavily on hybrid models that combine on-premises infrastructure with cloud-based solutions, offering greater flexibility and scalability.
Conclusion
Remote access behind router is a vital component of modern networking, enabling users to connect to their networks securely and efficiently from anywhere in the world. By understanding the principles of remote access and following best practices, you can establish a robust and reliable connection that meets your needs.
We encourage you to share your thoughts and experiences in the comments section below. For more in-depth guides and expert advice, explore our other articles on networking and cybersecurity. Together, let's build a safer and more connected digital future!