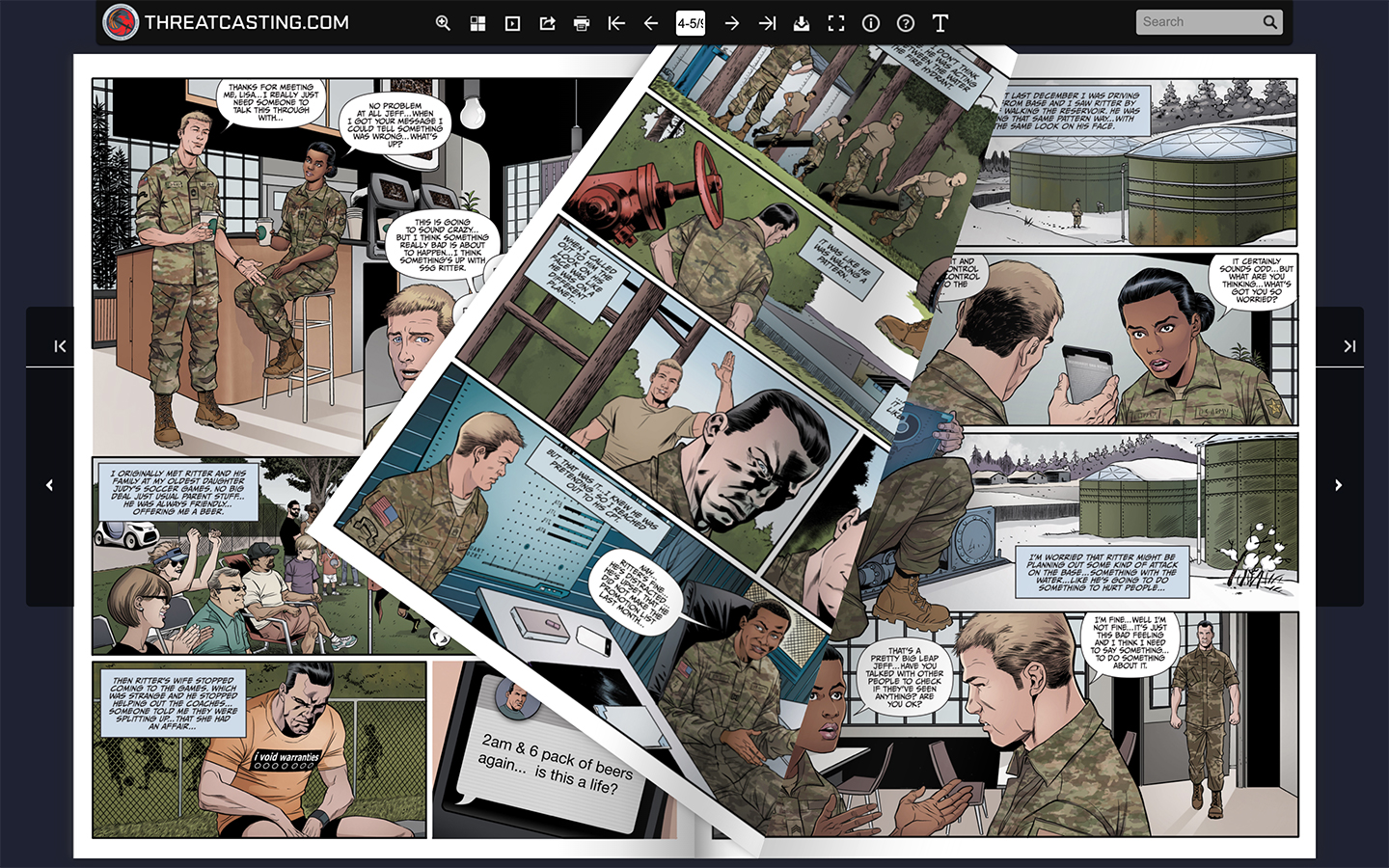
The potential insider threat before an incident is a critical concern for organizations worldwide. In today's digital age, businesses must recognize that the greatest cybersecurity risks often come from within their own walls. While external threats like hackers and malware receive significant attention, insider threats can be equally, if not more, damaging. Understanding the warning signs and taking proactive measures is essential to safeguarding sensitive information and maintaining operational integrity.
Insider threats are not limited to malicious actions by disgruntled employees. They can also arise from negligence, lack of awareness, or even well-meaning individuals who inadvertently expose vulnerabilities. This article will delve into the complexities of potential insider threats, exploring the risks, signs, and strategies to mitigate them effectively.
By the end of this article, you will have a comprehensive understanding of how to identify and address potential insider threats before they escalate into full-blown incidents. Whether you're a business owner, IT professional, or security analyst, this guide will equip you with the knowledge and tools to protect your organization from internal risks.
Read also:Jimmy Fallon Political Party 2024 Exploring The Connection Between Comedy And Politics
Table of Contents
- Understanding the Concept of Insider Threat
- Types of Insider Threats
- Warning Signs of Potential Insider Threats
- Risk Factors Contributing to Insider Threats
- The Impact of Insider Threats on Organizations
- Detecting Potential Insider Threats Before an Incident
- Strategies for Mitigating Insider Threats
- Technology Solutions for Insider Threat Detection
- Best Practices for Managing Insider Threats
- Conclusion and Call to Action
Understanding the Concept of Insider Threat
An insider threat refers to a risk posed by individuals within an organization who have authorized access to its systems, data, or facilities. These individuals may intentionally or unintentionally cause harm to the organization's assets, reputation, or operations. Understanding the concept of insider threats is the first step in developing an effective defense strategy.
Insider threats can manifest in various forms, including data breaches, intellectual property theft, sabotage, and espionage. Organizations must recognize that insider threats are not limited to employees but can also involve contractors, vendors, or partners with access to sensitive information.
Why Insider Threats Are Dangerous
Insider threats are particularly dangerous because they exploit trust and authorized access. Unlike external attackers, insiders often have a deep understanding of an organization's systems, processes, and vulnerabilities, making them more effective at causing harm.
Types of Insider Threats
Insider threats can be categorized into three main types: malicious insiders, negligent insiders, and compromised insiders. Each type presents unique challenges and requires tailored approaches for detection and mitigation.
Malicious Insiders
Malicious insiders deliberately exploit their access to cause harm. They may steal sensitive data, disrupt operations, or engage in espionage for personal or financial gain.
Negligent Insiders
Negligent insiders unintentionally expose vulnerabilities through carelessness or lack of awareness. Common examples include falling victim to phishing attacks, misconfiguring systems, or mishandling sensitive information.
Read also:Ticket 2021 Websites For Gamificationsummit Your Ultimate Guide To Attending The Event
Compromised Insiders
Compromised insiders are those whose credentials or devices have been hijacked by external attackers. These individuals may unknowingly contribute to security breaches by providing unauthorized access to internal systems.
Warning Signs of Potential Insider Threats
Identifying potential insider threats before an incident requires vigilance and proactive monitoring. Below are some common warning signs that organizations should watch out for:
- Unusual access patterns or login activity outside normal working hours
- Excessive data downloads or transfers to external devices or cloud storage
- Repeated violations of security policies or procedures
- Unexplained access to restricted areas or systems
- Changes in behavior or attitude, such as increased stress or dissatisfaction
Risk Factors Contributing to Insider Threats
Certain risk factors increase the likelihood of insider threats occurring within an organization. Understanding these factors is crucial for implementing effective preventive measures.
- Lack of employee training and awareness
- Inadequate access controls and monitoring systems
- Weak cybersecurity policies and enforcement
- High employee turnover or dissatisfaction
- Insufficient oversight of third-party vendors and contractors
The Impact of Insider Threats on Organizations
Insider threats can have devastating consequences for organizations, ranging from financial losses to reputational damage. Below are some key impacts:
- Data breaches leading to loss of sensitive information
- Disruption of critical operations and services
- Legal and regulatory penalties for non-compliance
- Decreased trust and confidence from customers and partners
- Increased costs associated with incident response and recovery
Detecting Potential Insider Threats Before an Incident
Early detection is critical to preventing insider threats from escalating into incidents. Organizations should implement a combination of behavioral analytics, monitoring tools, and employee reporting mechanisms to identify suspicious activities.
Behavioral analytics can help detect anomalies in user activity by comparing current behavior against established baselines. This technology enables organizations to flag potential insider threats before they cause harm.
Implementing User Activity Monitoring
User activity monitoring involves tracking and analyzing employee actions within an organization's systems. This includes monitoring file access, email communications, and network activity to identify unusual patterns that may indicate insider threats.
Strategies for Mitigating Insider Threats
Organizations can mitigate insider threats by adopting a multi-layered approach that combines technical controls, policy enforcement, and employee engagement. Below are some effective strategies:
- Implementing least privilege access to limit unnecessary system access
- Conducting regular security awareness training for all employees
- Establishing clear security policies and enforcing them consistently
- Performing background checks on employees and contractors
- Encouraging a culture of reporting suspicious activities without fear of retaliation
Technology Solutions for Insider Threat Detection
Advanced technology solutions play a vital role in detecting and mitigating insider threats. Organizations can leverage tools such as Data Loss Prevention (DLP), User and Entity Behavior Analytics (UEBA), and Security Information and Event Management (SIEM) systems to enhance their security posture.
These technologies provide real-time monitoring, threat detection, and incident response capabilities, enabling organizations to address potential insider threats proactively.
Benefits of Using UEBA for Insider Threat Detection
User and Entity Behavior Analytics (UEBA) uses machine learning algorithms to analyze user behavior and identify anomalies that may indicate insider threats. This technology offers several benefits, including:
- Proactive detection of suspicious activities
- Reduced false positives through advanced analytics
- Enhanced visibility into user actions across systems
Best Practices for Managing Insider Threats
Managing insider threats effectively requires a combination of best practices and continuous improvement. Below are some recommended practices for organizations:
- Regularly review and update security policies and procedures
- Conduct periodic risk assessments to identify vulnerabilities
- Implement a robust incident response plan to address insider threats
- Foster a culture of security awareness and accountability
- Invest in employee training and development programs
Conclusion and Call to Action
In conclusion, understanding and addressing potential insider threats before an incident is essential for protecting organizational assets and maintaining operational integrity. By recognizing the warning signs, implementing effective mitigation strategies, and leveraging advanced technology solutions, organizations can significantly reduce their risk exposure.
We encourage you to take action by reviewing your current security measures, enhancing employee training programs, and adopting best practices for managing insider threats. Share your thoughts and experiences in the comments section below, and explore other informative articles on our website for further guidance.