SSH (Secure Shell) is one of the most secure methods to remotely access and manage IoT devices like the Raspberry Pi from a Windows computer. Whether you're a beginner or an advanced user, understanding how to set up SSH for your Raspberry Pi can significantly enhance your ability to manage remote devices. This article provides a comprehensive guide on setting up SSH for Raspberry Pi, downloading necessary software, and managing IoT devices remotely.
In the era of smart homes and connected devices, the ability to control and interact with IoT devices remotely is essential. Raspberry Pi, with its versatility and affordability, has become a popular choice for developers and hobbyists alike. By enabling SSH on your Raspberry Pi, you can execute commands, transfer files, and manage your IoT setup without needing physical access to the device.
This article delves into the step-by-step process of setting up SSH for Raspberry Pi, downloading the required tools on Windows, and ensuring a seamless remote connection. We'll also explore some advanced tips to enhance security and optimize performance.
Read also:Kyren Wilson Family A Comprehensive Look Into The Life Of The Snooker Sensation
Table of Contents
- Introduction to SSH
- Raspberry Pi SSH Setup
- Download SSH Client for Windows
- Connecting to Raspberry Pi via SSH
- Securing Your SSH Connection
- Troubleshooting Common Issues
- Advanced SSH Features
- Alternatives to SSH
- Use Cases for Remote IoT Management
- Conclusion and Next Steps
Introduction to SSH
SSH, or Secure Shell, is a cryptographic network protocol used to secure communication between two devices over an unsecured network. It provides a safe and encrypted way to access remote servers, making it ideal for managing IoT devices like Raspberry Pi.
For users who want to control their Raspberry Pi remotely, SSH eliminates the need for a monitor, keyboard, and mouse. Instead, you can connect to your Raspberry Pi from any computer with an SSH client installed, such as Windows.
One of the key advantages of SSH is its robust security features, including encryption for data transfer and authentication mechanisms to ensure only authorized users can access the device.
Raspberry Pi SSH Setup
Enabling SSH on Raspberry Pi
Before you can connect to your Raspberry Pi via SSH, you need to enable the SSH service. Here's how you can do it:
- Insert the microSD card containing the Raspberry Pi OS into your computer.
- Create an empty file named "ssh" (without any file extension) in the root directory of the boot partition.
- Eject the SD card and insert it back into the Raspberry Pi.
Once the Raspberry Pi boots up, SSH will be enabled automatically.
Updating Raspberry Pi OS
It's always a good idea to update your Raspberry Pi OS before setting up SSH. Run the following commands in the terminal:
Read also:Vika Y Vova Video Original A Comprehensive Look At Their Rise And Impact
sudo apt updatesudo apt upgrade
This ensures that your system is up-to-date and compatible with the latest SSH protocols.
Download SSH Client for Windows
Windows 10 and later versions come with an integrated SSH client. To check if SSH is already installed on your system:
- Open Command Prompt or PowerShell.
- Type
sshand press Enter. If the command is recognized, SSH is already installed.
If SSH is not installed, you can enable it by following these steps:
- Go to Settings > Apps > Optional Features.
- Select "Add a feature" and search for "OpenSSH Client."
- Install the OpenSSH Client.
Alternatively, you can use third-party SSH clients like PuTTY, which offers additional features and a user-friendly interface.
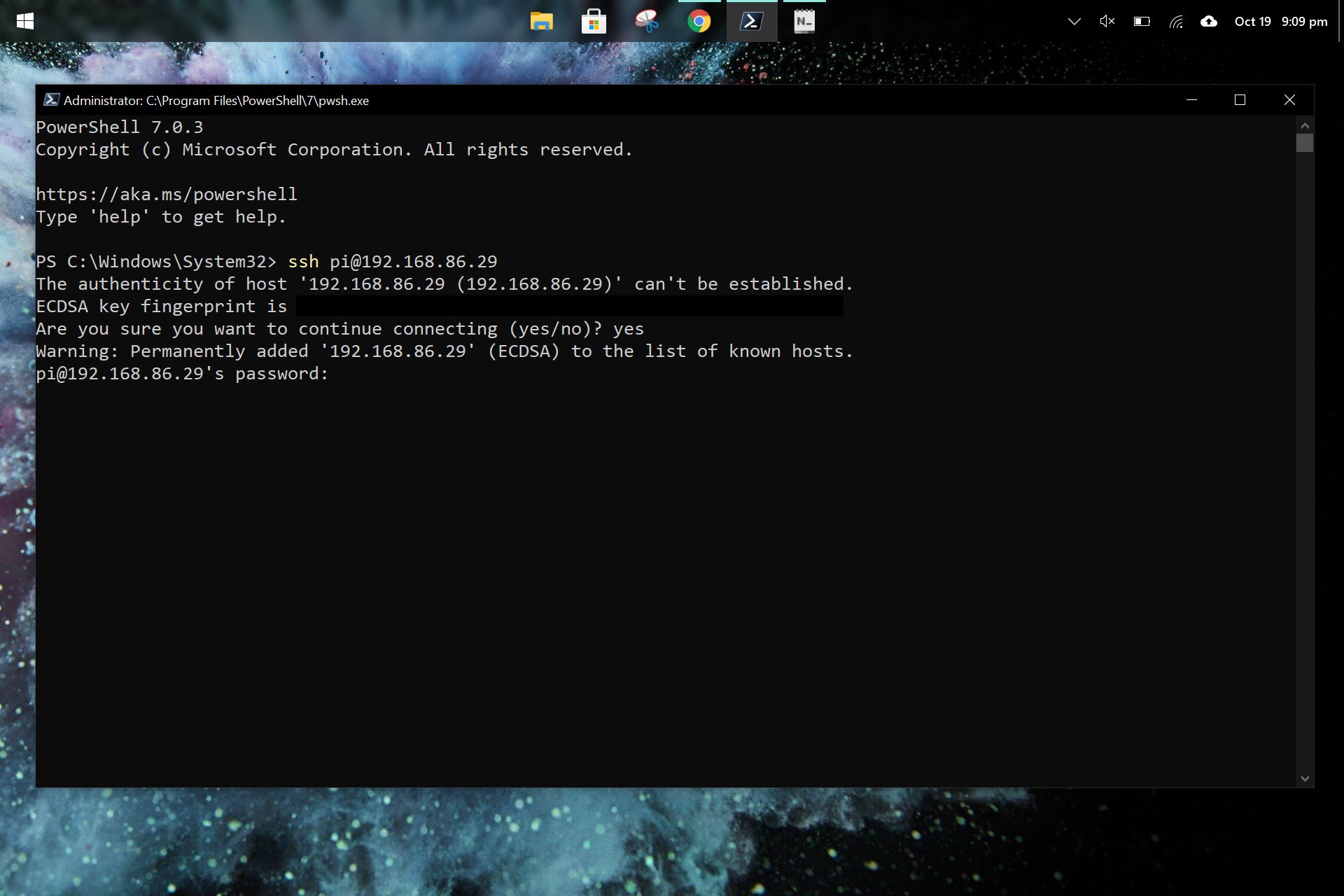
Connecting to Raspberry Pi via SSH
Identifying Raspberry Pi's IP Address
To connect to your Raspberry Pi via SSH, you need to know its IP address. You can find the IP address by:
- Checking the router's admin page.
- Using the command
hostname -Ion the Raspberry Pi terminal.
Once you have the IP address, you can connect to your Raspberry Pi from Windows using the following command in Command Prompt or PowerShell:
ssh pi@
Replace
Authentication
When connecting for the first time, you'll be prompted to accept the Raspberry Pi's RSA key. Type "yes" and press Enter. You'll then be asked to enter the password for the Raspberry Pi user account (default: "raspberry").
Securing Your SSH Connection
While SSH is inherently secure, there are additional steps you can take to enhance security:
- Change the Default Password: Update the default "raspberry" password to something more secure.
- Disable Root Login: Edit the SSH configuration file (
/etc/ssh/sshd_config) and setPermitRootLoginto "no." - Use Key-Based Authentication: Generate SSH keys on your Windows machine and copy the public key to your Raspberry Pi.
These measures will help protect your Raspberry Pi from unauthorized access.
Troubleshooting Common Issues
Connection Refused
If you receive a "Connection refused" error, ensure that:
- SSH is enabled on the Raspberry Pi.
- The IP address is correct.
- Firewall settings on both the Raspberry Pi and the network allow SSH connections (port 22).
Authentication Failure
If you encounter authentication issues, double-check the username and password. If you're using key-based authentication, ensure that the public key is correctly copied to the Raspberry Pi's ~/.ssh/authorized_keys file.
Advanced SSH Features
Port Forwarding
SSH can be used for port forwarding, allowing you to securely access services running on your Raspberry Pi from your Windows machine. For example:
ssh -L 8080:localhost:80 pi@
This command forwards traffic from port 80 on the Raspberry Pi to port 8080 on your Windows machine.
Tunneling
SSH tunneling can be used to bypass firewalls and access restricted services. It's particularly useful for accessing IoT devices in remote networks.
Alternatives to SSH
While SSH is the most popular method for remote access, there are alternatives worth considering:
- VNC (Virtual Network Computing): Provides a graphical interface for remote access.
- Web-based Interfaces: Some IoT devices come with web-based management interfaces.
- MQTT: A lightweight messaging protocol ideal for IoT applications.
Each alternative has its own advantages and disadvantages, so choose the one that best fits your needs.
Use Cases for Remote IoT Management
Remote management of IoT devices using SSH has numerous applications, including:
- Home Automation: Control smart home devices like lights, thermostats, and security systems.
- Environmental Monitoring: Collect data from sensors deployed in remote locations.
- Industrial Automation: Monitor and control industrial processes from a central location.
By leveraging SSH, you can efficiently manage and maintain your IoT infrastructure without the need for physical access.
Conclusion and Next Steps
Setting up SSH for Raspberry Pi on Windows is a straightforward process that opens up a world of possibilities for remote IoT device management. By following the steps outlined in this article, you can securely connect to your Raspberry Pi, execute commands, and manage your IoT setup from anywhere in the world.
We encourage you to explore advanced SSH features, such as port forwarding and tunneling, to further enhance your remote management capabilities. Additionally, consider implementing additional security measures to protect your devices from unauthorized access.
Feel free to leave a comment below if you have any questions or suggestions. Don't forget to share this article with your friends and colleagues who might find it useful. For more tips and tutorials, explore our other articles on IoT and Raspberry Pi.