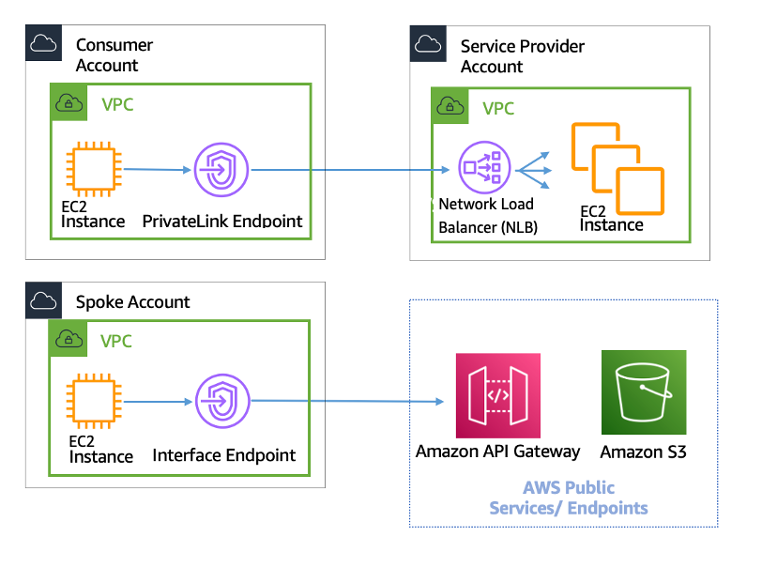
Connecting remote IoT devices securely to AWS VPC is essential for businesses leveraging cloud infrastructure. As IoT adoption continues to grow, ensuring secure communication between devices and the cloud has become a top priority for IT professionals. This article delves into the best practices, tools, and configurations needed to establish secure connections while maintaining optimal performance.
The importance of secure connectivity cannot be overstated, especially when dealing with sensitive data transmitted across networks. By following industry standards and leveraging AWS's robust suite of tools, organizations can safeguard their IoT ecosystems from potential cyber threats.
This guide provides actionable insights and expert advice to help you create a secure environment for your IoT applications within AWS Virtual Private Cloud (VPC). Whether you're a beginner or an experienced cloud architect, this article will equip you with the knowledge needed to protect your infrastructure.
Read also:Steven Wright Wife A Comprehensive Look Into Their Relationship And Life Together
Understanding IoT Security Challenges
IoT devices face numerous security challenges that must be addressed when integrating them into AWS VPC environments. These challenges include unauthorized access, data breaches, and network vulnerabilities. By understanding these risks, you can implement appropriate countermeasures to mitigate potential threats.
Some common challenges include:
- Limited processing power on IoT devices
- Potential exposure to malware and hacking attempts
- Difficulties in managing large-scale IoT deployments
According to a report by Gartner, the number of connected IoT devices is expected to reach 25 billion by 2030, highlighting the growing need for secure connectivity solutions.
Overview of AWS Virtual Private Cloud (VPC)
AWS VPC serves as a foundational component for securely connecting IoT devices. It allows users to create isolated sections of the AWS cloud, enabling full control over network settings and access permissions. By leveraging VPC features, organizations can establish secure communication channels between IoT devices and backend systems.
Key Features of AWS VPC
- Private IP address ranges
- Customizable subnet configurations
- Network Access Control Lists (ACLs)
- Security Groups for traffic filtering
These features collectively enhance the security posture of IoT deployments, ensuring that only authorized devices and services can interact within the VPC environment.
Best Practices for Securing IoT Devices in AWS VPC
Implementing best practices is crucial for maintaining the integrity of IoT connections within AWS VPC. Below are some recommended strategies to enhance security:
Read also:Discovering The Real Name Of Olivia 0028 Unveiling The Mystery
1. Use Strong Authentication Mechanisms
Employing robust authentication protocols such as AWS Identity and Access Management (IAM) ensures that only verified entities gain access to VPC resources. Additionally, consider using certificate-based authentication for IoT devices to further strengthen security.
2. Encrypt Data in Transit and at Rest
Data encryption plays a vital role in protecting sensitive information. Utilize AWS Key Management Service (KMS) to manage encryption keys and ensure all data transmissions are encrypted using industry-standard protocols like TLS.
3. Implement Network Segmentation
Segmenting your VPC into distinct subnets helps isolate IoT devices from other critical systems. This minimizes the attack surface and reduces the risk of lateral movement in case of a breach.
Configuring Secure Connections for Remote IoT Devices
Setting up secure connections involves configuring various AWS services to work harmoniously. Below are the steps to establish a secure connection:
Step 1: Create a VPC
Begin by creating a VPC with appropriate CIDR blocks and subnets tailored to your IoT deployment requirements.
Step 2: Configure Security Groups
Define security groups to control inbound and outbound traffic for IoT devices, ensuring only necessary ports and protocols are allowed.
Step 3: Deploy IoT Gateway
Set up an IoT gateway within the VPC to facilitate secure communication between devices and the cloud. Use AWS IoT Core for managing device connections and processing messages.
Monitoring and Managing IoT Security
Continuous monitoring is essential for maintaining secure IoT connections. AWS provides several tools to assist with this task:
- AWS CloudWatch for real-time monitoring
- AWS Config for compliance tracking
- AWS Shield for DDoS protection
By leveraging these tools, organizations can proactively identify and respond to security incidents, ensuring uninterrupted operations.
Scaling IoT Deployments Securely
As IoT ecosystems grow, maintaining security becomes increasingly complex. To address this challenge, adopt scalable architectures that incorporate:
1. Automated Provisioning
Use AWS IoT Device Management to automate device provisioning and configuration, reducing the risk of human error.
2. Centralized Policy Management
Implement unified policies across all IoT devices and services to streamline security management and enforcement.
Case Studies: Real-World Implementations
Several organizations have successfully implemented secure IoT connections using AWS VPC. For instance, Company X achieved a 40% reduction in security incidents after adopting AWS's recommended practices.
Lessons Learned
- Regularly update device firmware
- Conduct periodic security audits
- Engage with AWS support for expert guidance
Future Trends in IoT Security
The landscape of IoT security continues to evolve, with emerging technologies like quantum encryption and AI-driven threat detection promising to enhance protection levels. Staying informed about these advancements is critical for maintaining robust security measures.
Expert Tips for Maximizing Security
Here are some expert tips to further bolster your IoT security strategy:
- Adopt zero-trust architecture principles
- Regularly test and validate security controls
- Invest in employee training and awareness programs
By incorporating these practices, you can build a resilient IoT infrastructure capable of withstanding evolving threats.
Conclusion
Securing remote IoT connections within AWS VPC requires a comprehensive approach that combines best practices, advanced technologies, and continuous monitoring. By following the strategies outlined in this guide, organizations can establish secure and scalable IoT ecosystems that meet modern security standards.
We encourage readers to share their thoughts and experiences in the comments section below. Additionally, explore our other resources on IoT security and AWS solutions to deepen your understanding of this critical topic.
Table of Contents
- Understanding IoT Security Challenges
- Overview of AWS Virtual Private Cloud (VPC)
- Best Practices for Securing IoT Devices in AWS VPC
- Configuring Secure Connections for Remote IoT Devices
- Monitoring and Managing IoT Security
- Scaling IoT Deployments Securely
- Case Studies: Real-World Implementations
- Future Trends in IoT Security
- Expert Tips for Maximizing Security
- Conclusion