In today's interconnected world, securely connect remote IoT P2P Raspberry Pi download Mac has become a critical focus for developers and tech enthusiasts alike. The Internet of Things (IoT) continues to revolutionize how we interact with technology, and ensuring secure communication between devices is paramount. Whether you're setting up a home automation system or building a complex industrial solution, understanding how to create a secure peer-to-peer (P2P) connection on Raspberry Pi is essential.
This guide dives deep into the best practices for creating a secure P2P network using Raspberry Pi, particularly for macOS users. By following the steps outlined here, you can ensure your IoT devices remain protected against unauthorized access and cyber threats. From configuring firewalls to implementing encryption protocols, we'll cover it all.
Whether you're a beginner or an advanced user, this article provides actionable insights to help you set up and manage your IoT ecosystem safely. Let's explore how you can achieve seamless and secure communication between devices.
Read also:The Ultimate Guide To Tiniest Bikini Style Confidence And Fashion Trends
Table of Contents:
- Introduction to IoT and Secure Connections
- Understanding Raspberry Pi and Its Role in IoT
- Creating a Secure P2P Connection
- Importance of Encryption in IoT
- Setting Up Raspberry Pi on macOS
- Configuring Firewalls for Enhanced Security
- Troubleshooting Common Issues
- Best Practices for IoT Security
- Recommended Resources for Further Learning
- Conclusion and Next Steps
Introduction to IoT and Secure Connections
Why IoT Security Matters
As more devices become connected to the internet, the risk of cyberattacks increases exponentially. The Internet of Things (IoT) encompasses a vast array of devices, from smart thermostats to industrial sensors, all of which require secure communication channels. A breach in one device can compromise the entire network, making security a top priority.
For example, in 2021, the number of IoT devices surpassed 12 billion globally, according to Statista. With such widespread adoption, ensuring that these devices communicate securely is crucial. This is where securely connect remote IoT P2P Raspberry Pi download Mac comes into play.
The Role of Peer-to-Peer (P2P) Networks
Peer-to-peer (P2P) networks allow devices to communicate directly with each other without relying on a central server. This setup reduces latency and enhances efficiency, making it ideal for IoT applications. However, P2P networks must be secured to prevent unauthorized access and data breaches.
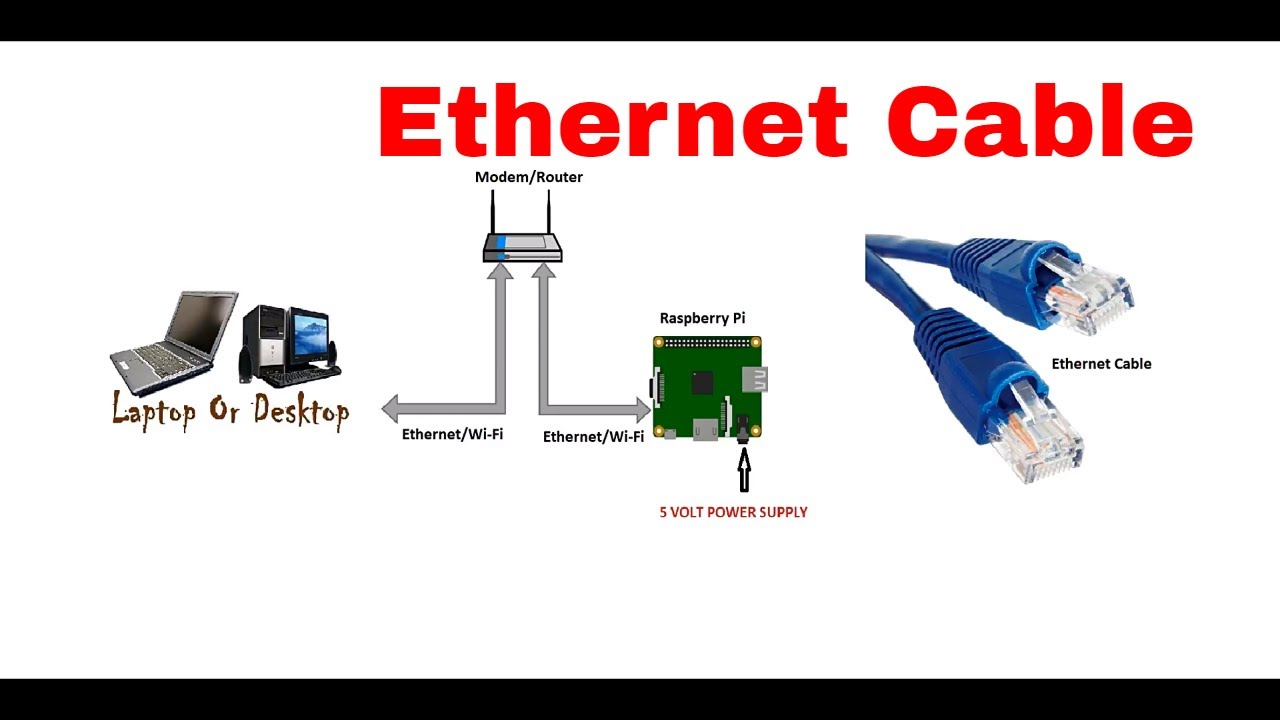
By leveraging Raspberry Pi, a versatile and affordable single-board computer, you can create a secure P2P network tailored to your needs. This guide will walk you through the process step by step, ensuring your IoT ecosystem remains protected.
Understanding Raspberry Pi and Its Role in IoT
What Is Raspberry Pi?
Raspberry Pi is a small, low-cost computer that has gained immense popularity among hobbyists, educators, and developers. Its versatility makes it an excellent choice for IoT projects, from home automation to industrial automation.
Read also:Top Site For Ticket Sale Gamificationsummit Your Ultimate Guide To Attending The Event
Key features of Raspberry Pi include:
- Compact size
- Low power consumption
- Support for multiple operating systems
- Extensive community support
Using Raspberry Pi for IoT Projects
Raspberry Pi serves as the backbone of many IoT projects due to its ability to handle complex tasks while remaining cost-effective. By integrating Raspberry Pi into your IoT network, you can achieve secure and reliable communication between devices.
For macOS users, setting up Raspberry Pi involves a few additional steps, but the process is straightforward with the right tools and resources.
Creating a Secure P2P Connection
Steps to Establish a Secure P2P Network
To create a secure P2P connection using Raspberry Pi, follow these steps:
- Install the necessary software on your Raspberry Pi.
- Configure the network settings to enable P2P communication.
- Implement encryption protocols to protect data transmission.
- Test the connection to ensure it is functioning correctly.
Each of these steps is crucial to ensuring the security and reliability of your P2P network. Let's explore them in more detail below.
Choosing the Right Encryption Protocol
Encryption is a vital component of any secure P2P network. Popular encryption protocols for IoT include:
- SSL/TLS
- SSH
- IPsec
Selecting the appropriate protocol depends on your specific use case and the level of security required. For most IoT applications, SSL/TLS provides a robust and efficient solution.
Importance of Encryption in IoT
Encryption plays a critical role in securing IoT devices and networks. By encrypting data transmitted between devices, you can prevent unauthorized access and ensure the privacy of sensitive information.
According to a report by Gartner, over 20% of organizations will have experienced an IoT-related security breach by 2025. Implementing strong encryption protocols is one of the most effective ways to mitigate this risk.
Setting Up Raspberry Pi on macOS
Preparing Your macOS Environment
Before setting up Raspberry Pi on macOS, ensure your system meets the following requirements:
- macOS version 10.13 or later
- A microSD card with at least 16GB capacity
- Raspberry Pi Imager software
Once you have everything ready, follow these steps to set up your Raspberry Pi:
- Download and install Raspberry Pi Imager on your Mac.
- Insert the microSD card into your Mac.
- Launch Raspberry Pi Imager and select the desired operating system.
- Write the image to the microSD card and insert it into your Raspberry Pi.
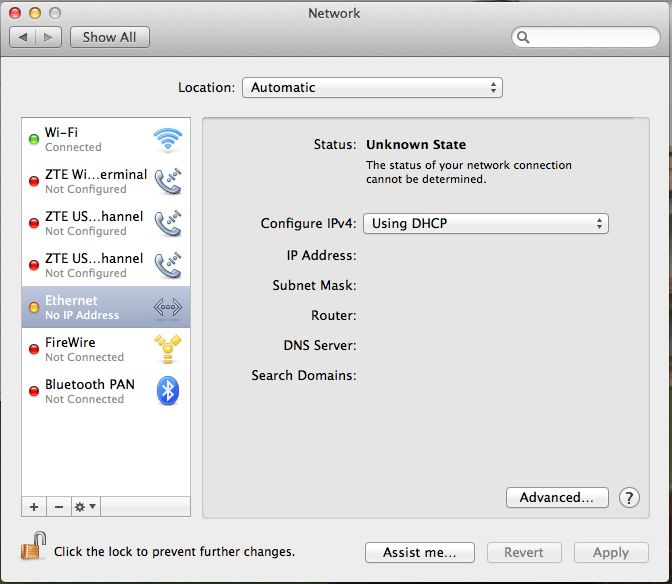
Connecting Raspberry Pi to macOS
After setting up Raspberry Pi, connect it to your Mac using an Ethernet cable or Wi-Fi. You can then access the Raspberry Pi interface via SSH or VNC, depending on your preference.
Configuring Firewalls for Enhanced Security
Firewalls are essential for protecting your IoT network from unauthorized access. By configuring a firewall on your Raspberry Pi, you can control incoming and outgoing traffic, ensuring only trusted devices can communicate with your network.
Popular firewall solutions for Raspberry Pi include:
- UFW (Uncomplicated Firewall)
- iptables
For beginners, UFW provides a simple and effective way to manage firewall rules. Advanced users may prefer iptables for more granular control.
Troubleshooting Common Issues
Connection Problems
If you encounter issues connecting to your Raspberry Pi, check the following:
- Ensure the microSD card is properly inserted.
- Verify the network settings are correct.
- Check for any firewall rules blocking the connection.
Performance Issues
Slow performance on Raspberry Pi can be caused by insufficient resources or misconfigured settings. To optimize performance:
- Upgrade the microSD card to a faster model.
- Disable unnecessary services running in the background.
- Update the operating system and installed packages regularly.
Best Practices for IoT Security
To ensure the security of your IoT network, follow these best practices:
- Use strong, unique passwords for all devices.
- Regularly update firmware and software to patch vulnerabilities.
- Limit access to your network to trusted devices only.
- Monitor network activity for signs of unauthorized access.
By adhering to these guidelines, you can significantly reduce the risk of security breaches in your IoT ecosystem.
Recommended Resources for Further Learning
For those looking to deepen their understanding of IoT security and Raspberry Pi, consider exploring the following resources:
Conclusion and Next Steps
Securing your IoT network is essential in today's interconnected world. By following the steps outlined in this guide, you can create a secure P2P connection using Raspberry Pi, tailored to your specific needs. Whether you're setting up a home automation system or building an industrial solution, ensuring the security of your devices is paramount.
We encourage you to share your thoughts and experiences in the comments below. Additionally, explore our other articles for more insights into IoT and cybersecurity. Together, we can build a safer and more connected future.