In the rapidly evolving world of technology, the ability to securely connect remote IoT P2P Raspberry Pi has become a crucial skill for developers and enthusiasts alike. Whether you're setting up a home automation system or creating a robust network for data transfer, understanding how to establish secure connections is paramount. This guide will walk you through the steps to ensure your IoT devices remain safe and efficient.
As more businesses and individuals adopt IoT solutions, ensuring the security of these devices becomes even more critical. The rise in cyber threats demands a proactive approach to safeguarding your network and data. This article will delve into the best practices for securely connecting your Raspberry Pi to remote IoT devices, ensuring a seamless peer-to-peer (P2P) connection that can be easily downloaded and deployed on Mac for free.
Whether you're a beginner or an experienced user, this guide offers practical insights and actionable steps to enhance your IoT setup. From understanding the basics of Raspberry Pi to exploring advanced security protocols, we'll cover everything you need to know to establish a secure connection.
Read also:Real Estate Vs Usain Bolt The Ultimate Investment Showdown
Understanding Raspberry Pi and IoT
Raspberry Pi has revolutionized the way we interact with technology, offering a cost-effective solution for building IoT projects. At its core, Raspberry Pi is a small, single-board computer that can be programmed to perform a wide range of functions. When combined with IoT, it creates a powerful platform for innovation.
What is Raspberry Pi?
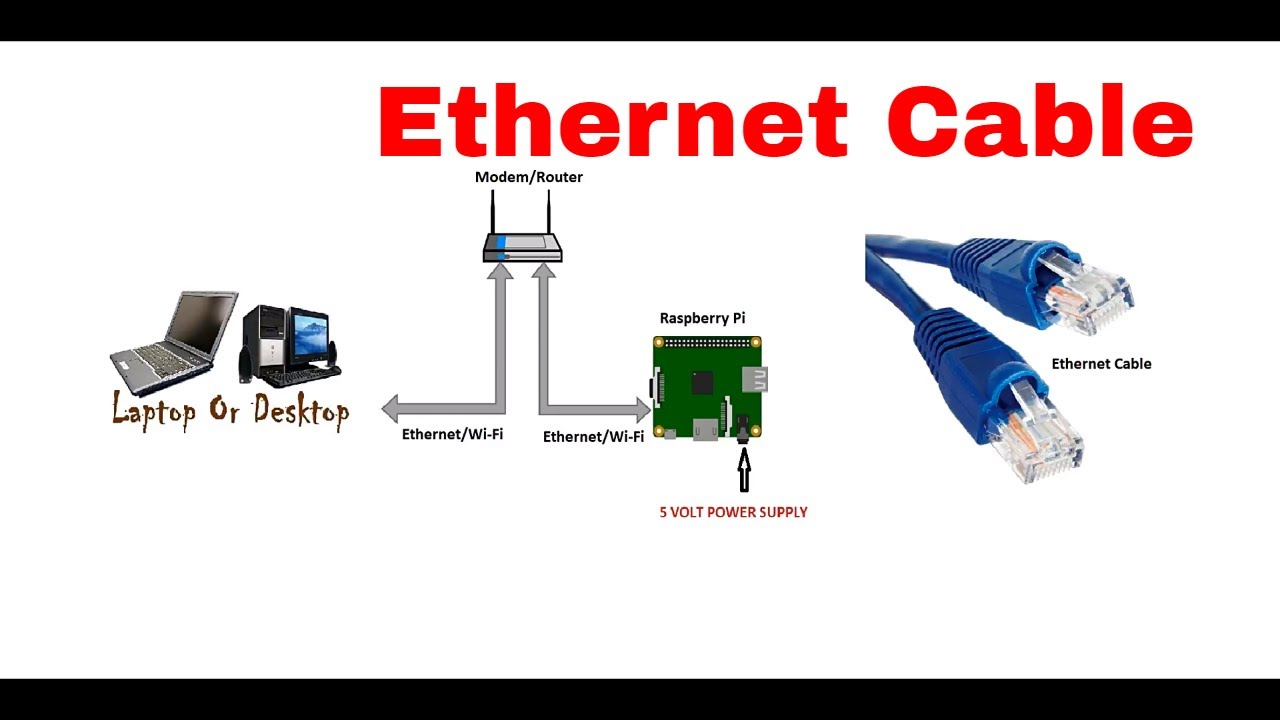
Raspberry Pi is a series of credit-card-sized single-board computers developed by the Raspberry Pi Foundation. Initially designed to promote the teaching of basic computer science in schools, it quickly gained popularity among hobbyists and professionals alike. The device is equipped with various ports, including USB, HDMI, and Ethernet, making it versatile for a wide range of applications.
Key Features of Raspberry Pi
- Compact and lightweight design
- Multiple input/output options
- Support for various operating systems
- Highly customizable and programmable
Why Secure Connections are Essential for IoT Devices
In the realm of IoT, security cannot be overlooked. As devices become more interconnected, the potential for cyberattacks increases exponentially. Securing your IoT devices is not just about protecting data; it's about safeguarding your entire network infrastructure. A single breach can lead to significant financial losses and reputational damage.
Common IoT Security Threats
- Unauthorized access to devices
- Data breaches and theft
- Malware and ransomware attacks
- Denial of Service (DoS) attacks
Best Practices for IoT Security
Implementing robust security measures is essential for protecting your IoT devices. Some best practices include:
- Regularly updating firmware and software
- Using strong, unique passwords
- Implementing encryption protocols
- Limiting device access to trusted networks
Setting Up Raspberry Pi for Secure IoT Connections
Setting up Raspberry Pi for secure IoT connections involves several steps. From initial configuration to implementing advanced security protocols, each step plays a crucial role in ensuring the safety of your network. Below is a detailed guide to help you through the process.
Step 1: Initial Setup
Begin by installing the latest version of Raspberry Pi OS on your device. Ensure that all necessary drivers and dependencies are installed to support IoT functionalities. Additionally, configure your network settings to allow remote access securely.
Read also:Erin Jayne Plummer The Rising Star Of Hollywood
Step 2: Implementing Encryption
Encryption is vital for securing data transmission between IoT devices. Use protocols such as TLS (Transport Layer Security) or SSL (Secure Sockets Layer) to encrypt data in transit. This ensures that even if intercepted, the data remains unreadable to unauthorized parties.
Peer-to-Peer (P2P) Connections with Raspberry Pi
Establishing a P2P connection with Raspberry Pi allows for direct communication between devices without relying on centralized servers. This not only enhances security but also reduces latency and bandwidth usage.
Advantages of P2P Connections
- Reduced reliance on third-party servers
- Improved data privacy and security
- Lower latency and faster data transfer
Configuring P2P on Raspberry Pi
To configure P2P on Raspberry Pi, you'll need to install and set up software such as WebRTC or libp2p. These tools facilitate secure, direct communication between devices. Follow the official documentation to ensure proper installation and configuration.
Downloading and Installing Raspberry Pi Software on Mac
Downloading and installing Raspberry Pi software on a Mac is straightforward. With the availability of free tools and resources, setting up your Raspberry Pi for IoT projects has never been easier.
Step 1: Downloading Raspberry Pi Imager
Begin by downloading the Raspberry Pi Imager from the official Raspberry Pi website. This tool simplifies the process of writing the operating system to an SD card, ensuring a seamless installation.
Step 2: Writing the OS to an SD Card
Once the Raspberry Pi Imager is installed, insert an SD card into your Mac and select the appropriate OS image. Follow the on-screen instructions to write the image to the SD card, ensuring all data is properly transferred.
Free Resources for Raspberry Pi IoT Projects
There are numerous free resources available for Raspberry Pi IoT projects. From open-source software to community forums, these resources provide valuable insights and support for developers and enthusiasts.
Popular Open-Source Software
- Node-RED: A flow-based programming tool for IoT
- MQTT: A lightweight messaging protocol for IoT
- Home Assistant: A home automation platform for IoT
Community Forums and Support
Engaging with the Raspberry Pi community can provide invaluable support and inspiration for your IoT projects. Platforms like Reddit, Stack Overflow, and the official Raspberry Pi forums offer a wealth of knowledge and assistance.
Data Security and Privacy in IoT
Data security and privacy are paramount in IoT. As devices continue to generate vast amounts of data, ensuring its protection is crucial. Implementing robust security measures and adhering to privacy regulations can help mitigate risks.
Regulatory Compliance
Compliance with data protection regulations such as GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) is essential for businesses operating in IoT. Understanding and implementing these regulations can help safeguard user data and maintain trust.
Future Trends in Secure IoT Connections
The future of IoT is bright, with advancements in technology driving innovation in secure connections. From edge computing to AI-driven security solutions, the possibilities are endless.
Emerging Technologies
- Edge computing for enhanced data processing
- AI-powered security for real-time threat detection
- Blockchain for secure data transactions
Challenges and Opportunities
While the future looks promising, challenges such as scalability and interoperability must be addressed. By embracing new technologies and fostering collaboration, the IoT industry can continue to grow and thrive.
Conclusion
Securing IoT connections with Raspberry Pi is essential for protecting your network and data. By following the steps outlined in this guide, you can establish a robust and secure connection that ensures the safety of your IoT devices. Remember to regularly update your software and implement encryption protocols to safeguard against potential threats.
We encourage you to share your thoughts and experiences in the comments below. Your feedback is invaluable in helping us improve and expand our content. Additionally, feel free to explore our other articles for more insights and tips on IoT and Raspberry Pi projects.
Table of Contents
- Understanding Raspberry Pi and IoT
- Why Secure Connections are Essential for IoT Devices
- Setting Up Raspberry Pi for Secure IoT Connections
- Peer-to-Peer (P2P) Connections with Raspberry Pi
- Downloading and Installing Raspberry Pi Software on Mac
- Free Resources for Raspberry Pi IoT Projects
- Data Security and Privacy in IoT
- Future Trends in Secure IoT Connections
- Conclusion