RemoteIoT VPC SSH AWS has become a cornerstone in modern cloud computing infrastructure. As organizations increasingly adopt cloud-based solutions, understanding how to securely configure and manage Virtual Private Clouds (VPCs) with SSH access is critical. This comprehensive guide will take you through everything you need to know about setting up RemoteIoT VPC SSH on AWS, ensuring your network remains secure and efficient.
As businesses expand their digital footprints, the demand for remote access to IoT devices and cloud resources has surged. RemoteIoT VPC SSH AWS provides the necessary tools to establish secure connections between remote devices and cloud-based servers. This setup not only enhances security but also improves operational efficiency by enabling seamless communication between devices and the cloud.
This article will delve into the intricacies of RemoteIoT VPC SSH AWS, covering everything from basic concepts to advanced configurations. Whether you're a beginner or an experienced cloud engineer, this guide will equip you with the knowledge and skills needed to implement and manage RemoteIoT VPC SSH AWS effectively.
Read also:Steven Wright Wife A Comprehensive Look Into Their Relationship And Life Together
Table of Contents
- Introduction to VPC
- Understanding SSH
- RemoteIoT Overview
- AWS VPC Configuration
- SSH Access Setup
- Security Best Practices
- Troubleshooting Common Issues
- Scaling RemoteIoT VPC SSH
- Real-World Applications
- Future Trends
Introduction to VPC
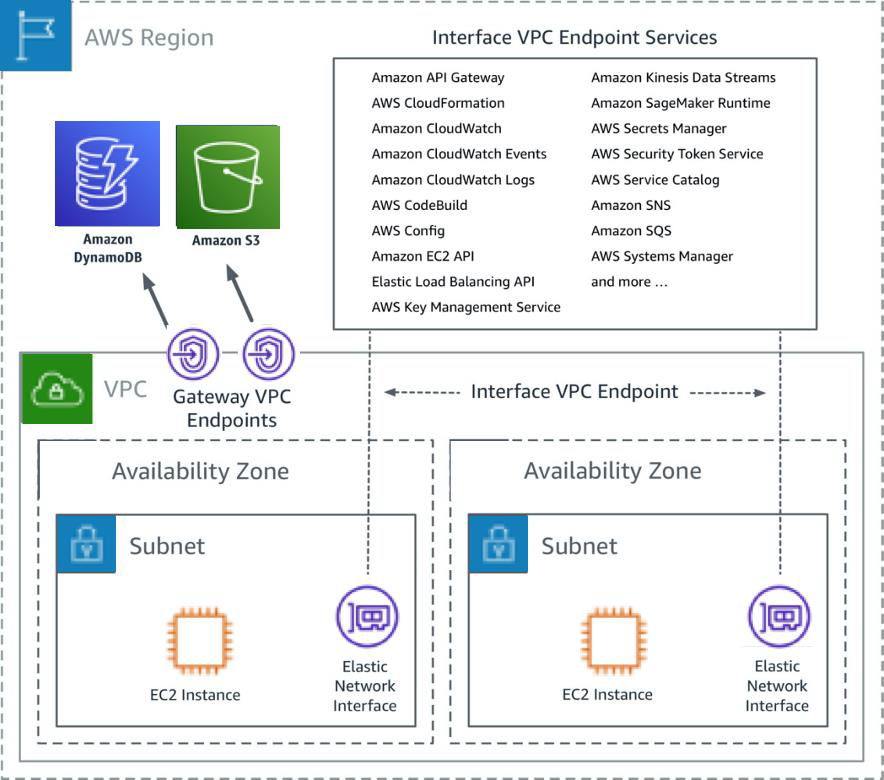
A Virtual Private Cloud (VPC) is a fundamental component of AWS infrastructure. It allows users to create an isolated section of the AWS cloud where they can launch AWS resources in a virtual network. This isolation enhances security and provides greater control over network configurations.
Key Features of VPC
- Customizable IP Address Ranges
- Subnet Creation
- Route Tables and Network Access Control Lists (ACLs)
- Internet Gateways and NAT Gateways
VPCs are essential for RemoteIoT VPC SSH AWS setups as they provide the foundation for secure and scalable network environments. By leveraging VPC features, organizations can ensure that their IoT devices and cloud resources are protected from unauthorized access.
Understanding SSH
Secure Shell (SSH) is a cryptographic network protocol used to establish secure connections between a client and a server. It provides encrypted communication, ensuring data integrity and confidentiality. In the context of RemoteIoT VPC SSH AWS, SSH is crucial for securely accessing and managing cloud resources.
Benefits of Using SSH
- Data Encryption
- Authentication Mechanisms
- Secure File Transfers
SSH is widely regarded as one of the most secure methods for remote access. Its robust encryption protocols and authentication mechanisms make it an ideal choice for securing RemoteIoT VPC SSH AWS environments.
RemoteIoT Overview
RemoteIoT refers to the practice of managing and monitoring IoT devices remotely. This approach is particularly useful for organizations that deploy IoT devices across geographically dispersed locations. By integrating RemoteIoT with VPC SSH AWS, businesses can achieve greater control and visibility over their IoT ecosystems.
Advantages of RemoteIoT
- Centralized Device Management
- Real-Time Data Monitoring
- Scalability and Flexibility
RemoteIoT VPC SSH AWS enables organizations to streamline their operations by providing a centralized platform for managing IoT devices. This integration enhances efficiency and reduces the risk of security breaches.
Read also:Bryant Hvac Systems A Comprehensive Guide To Reliable Climate Control Solutions
AWS VPC Configuration
Configuring a VPC on AWS involves several key steps. These include defining the IP address range, creating subnets, setting up route tables, and configuring security groups. Proper VPC configuration is essential for ensuring the security and performance of RemoteIoT VPC SSH AWS environments.
Steps to Configure VPC
- Create a New VPC
- Define Subnets
- Set Up Route Tables
- Configure Security Groups
By following these steps, organizations can create a secure and efficient VPC environment tailored to their specific needs. This setup forms the backbone of any successful RemoteIoT VPC SSH AWS implementation.
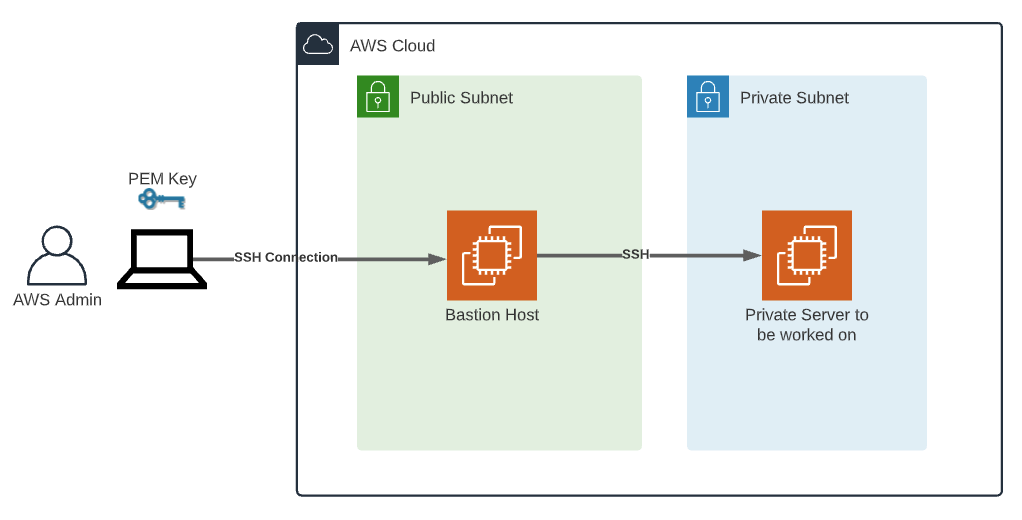
SSH Access Setup
Setting up SSH access for RemoteIoT VPC SSH AWS requires careful consideration of security and usability. Key components include generating SSH keys, configuring security groups, and establishing SSH connections.
Generating SSH Keys
SSH keys are cryptographic keys used for authenticating users and devices. To generate SSH keys, you can use tools like OpenSSL or the AWS Management Console. Once generated, these keys should be securely stored and distributed only to authorized personnel.
Configuring Security Groups
Security groups act as virtual firewalls for your AWS resources. When configuring security groups for SSH access, it's important to restrict access to specific IP addresses or ranges. This ensures that only trusted devices and users can establish SSH connections.
Security Best Practices
Implementing security best practices is critical for protecting RemoteIoT VPC SSH AWS environments. These practices include regular security audits, enforcing strong password policies, and monitoring network activity.
Key Security Measures
- Regular Security Audits
- Enforce Strong Password Policies
- Monitor Network Activity
By adhering to these best practices, organizations can significantly reduce the risk of security breaches and ensure the integrity of their RemoteIoT VPC SSH AWS setups.
Troubleshooting Common Issues
Despite careful planning and implementation, issues can arise in RemoteIoT VPC SSH AWS environments. Common problems include connectivity issues, authentication failures, and misconfigured security groups.
Solutions to Common Issues
- Check Network Connectivity
- Verify SSH Key Authenticity
- Review Security Group Configurations
By addressing these issues promptly, organizations can maintain the reliability and performance of their RemoteIoT VPC SSH AWS setups.
Scaling RemoteIoT VPC SSH
As organizations grow, so does the need to scale their RemoteIoT VPC SSH AWS environments. Scaling involves increasing resources, optimizing configurations, and implementing automation tools.
Strategies for Scaling
- Increase Resource Allocation
- Optimize Configurations
- Implement Automation Tools
By adopting these strategies, businesses can ensure that their RemoteIoT VPC SSH AWS environments remain scalable and efficient as they expand.
Real-World Applications
RemoteIoT VPC SSH AWS has numerous real-world applications across various industries. From smart cities to industrial automation, this technology is transforming how organizations manage and monitor IoT devices.
Industry Use Cases
- Smart Cities
- Industrial Automation
- Healthcare Monitoring
These applications demonstrate the versatility and potential of RemoteIoT VPC SSH AWS in addressing modern business challenges.
Future Trends
The future of RemoteIoT VPC SSH AWS is bright, with advancements in technology driving innovation and growth. Emerging trends include the integration of artificial intelligence, the adoption of edge computing, and the development of more secure authentication methods.
As these trends continue to evolve, organizations must remain adaptable and forward-thinking to fully leverage the capabilities of RemoteIoT VPC SSH AWS.
Conclusion
In conclusion, mastering RemoteIoT VPC SSH AWS is essential for organizations seeking to enhance their cloud computing infrastructure. By understanding the key concepts, implementing best practices, and staying informed about future trends, businesses can achieve secure and efficient RemoteIoT VPC SSH AWS setups.
We invite you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into cloud computing and IoT technologies. Together, let's build a smarter, more connected future.