RemoteIoT devices have become increasingly popular in recent years, offering a wide range of applications from home automation to industrial monitoring. As more businesses and individuals rely on these devices, understanding how to securely connect and manage them remotely is crucial. This tutorial will guide you step-by-step through the process of using SSH (Secure Shell) to manage your RemoteIoT devices effectively.
Whether you're a seasoned IT professional or a beginner exploring IoT technologies, mastering SSH is essential for maintaining secure communication with your RemoteIoT devices. This article will cover everything you need to know, from setting up SSH to troubleshooting common issues.
By the end of this guide, you'll have the knowledge and skills to confidently manage your RemoteIoT devices remotely while ensuring optimal security. Let's dive in!
Read also:Cindy Williams Cause Of Death A Detailed Look Into Her Life And Legacy
Table of Contents
- Introduction to RemoteIoT Devices
- What is SSH?
- Setting Up SSH on Your RemoteIoT Device
- Connecting to Your RemoteIoT Device via SSH
- Securing Your SSH Connection
- Common SSH Issues and How to Fix Them
- Advanced SSH Configurations
- Best Practices for Using SSH with RemoteIoT Devices
- Tools and Software for Managing SSH Connections
- The Future of RemoteIoT Devices and SSH
Introduction to RemoteIoT Devices
RemoteIoT devices are internet-connected gadgets designed to perform specific tasks without requiring physical intervention. These devices can range from simple sensors to complex industrial controllers. Their ability to operate independently and transmit data over the internet makes them indispensable in various sectors.
One of the key challenges with RemoteIoT devices is ensuring secure communication, especially when managing them remotely. This is where SSH comes into play, providing a robust framework for secure data exchange.
Why Use RemoteIoT Devices?
- Enhanced automation capabilities
- Reduced operational costs
- Improved data collection and analysis
- Increased scalability and flexibility
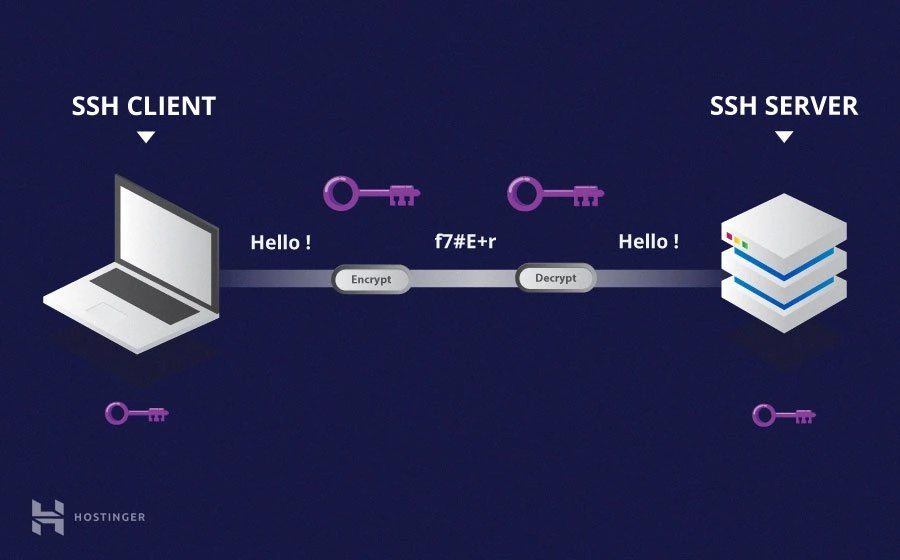
What is SSH?
SSH, or Secure Shell, is a network protocol that allows users to securely access and manage remote devices over an unsecured network. It encrypts all data transmitted between the client and server, ensuring confidentiality and integrity.
SSH is widely used in IT environments for tasks such as remote administration, file transfers, and secure tunneling. Its versatility and security features make it an ideal choice for managing RemoteIoT devices.
Key Features of SSH
- Data encryption
- Authentication mechanisms
- Command execution capabilities
Setting Up SSH on Your RemoteIoT Device
Before you can use SSH to manage your RemoteIoT device, you need to ensure that SSH is properly installed and configured. Most modern RemoteIoT devices come with SSH pre-installed, but some may require manual setup.
Here’s a step-by-step guide to setting up SSH:
Read also:Best Low Deflection Shafts Unleashing Your Golf Potential
- Log in to your RemoteIoT device via its web interface or local terminal.
- Install the SSH server if it's not already installed. For Linux-based devices, you can use the command:
sudo apt-get install openssh-server. - Start the SSH service using the command:
sudo service ssh start. - Verify that SSH is running by checking its status:
sudo service ssh status.
Connecting to Your RemoteIoT Device via SSH
Once SSH is set up on your RemoteIoT device, you can connect to it from any computer with an SSH client installed. Below are the steps to establish a connection:
Step 1: Obtain the Device's IP Address
You'll need the IP address of your RemoteIoT device to connect via SSH. This can usually be found in the device's settings or by running the command: ifconfig or ip addr.
Step 2: Use an SSH Client
On Windows, you can use PuTTY, while macOS and Linux users can use the built-in terminal. Enter the following command to connect:
ssh username@device_ip_addressReplace "username" with your device's login credentials and "device_ip_address" with the actual IP address.
Securing Your SSH Connection
While SSH is inherently secure, additional measures can be taken to enhance its security. Here are some best practices:
- Change the default SSH port (default is 22) to a non-standard port.
- Disable root login to prevent unauthorized access.
- Use public key authentication instead of passwords.
- Implement firewall rules to restrict access to specific IP addresses.
Public Key Authentication
Public key authentication involves generating a pair of keys: a public key and a private key. The public key is placed on the server, while the private key is kept securely on the client machine. This method eliminates the need for passwords, significantly reducing the risk of brute-force attacks.
Common SSH Issues and How to Fix Them
Even with proper configuration, SSH connections can sometimes encounter issues. Below are some common problems and their solutions:
Issue 1: Connection Refused
Cause: The SSH service may not be running or the port is blocked.
Solution: Check the SSH service status and ensure the firewall allows traffic on the SSH port.
Issue 2: Permission Denied
Cause: Incorrect login credentials or disabled password authentication.
Solution: Verify your username and password. If using public key authentication, ensure the public key is correctly placed in the authorized_keys file.
Advanced SSH Configurations
For users seeking more control over their SSH connections, advanced configurations can be implemented. These include:
- Setting up SSH tunnels for secure data transfer.
- Configuring SSH jump hosts for multi-hop connections.
- Customizing SSH settings in the ssh_config file.
SSH Tunnels
SSH tunnels allow you to securely forward traffic from one network to another. This is particularly useful when accessing services behind a firewall. To set up a tunnel, use the following command:
ssh -L local_port:destination_host:destination_port username@ssh_serverBest Practices for Using SSH with RemoteIoT Devices
To ensure optimal performance and security, follow these best practices:
- Regularly update your SSH server and client software.
- Monitor SSH logs for suspicious activity.
- Limit access to trusted IP addresses.
- Use strong, unique passwords or passphrase-protected keys.
Monitoring SSH Logs
SSH logs can provide valuable insights into connection attempts and potential security threats. On Linux systems, these logs are typically located in /var/log/auth.log. Regularly reviewing these logs can help identify and mitigate security risks.
Tools and Software for Managing SSH Connections
Several tools and software can simplify SSH management:
- Putty: A popular SSH client for Windows users.
- SSHFS: Allows you to mount remote file systems over SSH.
- Keychain: Manages SSH keys and passwords securely.
SSHFS for File Transfer
SSHFS enables you to access remote files as if they were local. This is particularly useful for managing files on your RemoteIoT device. To mount a remote directory, use the following command:
sshfs username@remote_host:/remote/directory /local/mountpointThe Future of RemoteIoT Devices and SSH
As technology continues to evolve, RemoteIoT devices will play an increasingly important role in various industries. The integration of advanced security protocols, such as SSH, will be crucial in ensuring their reliability and safety.
Future advancements may include:
- Enhanced encryption algorithms for SSH.
- Integration with AI-driven security systems.
- Increased interoperability with other IoT protocols.
Conclusion
In conclusion, mastering SSH is essential for anyone working with RemoteIoT devices. By following the steps outlined in this tutorial, you can securely manage your devices and protect sensitive data. Remember to adhere to best practices and regularly update your systems to stay ahead of potential threats.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, explore other articles on our site to deepen your knowledge of IoT technologies and security solutions.